We are having a very unusual problem on our network.
There are two sites: main office (1x SBS 2003 server and 20x PCs: a mixture of Win7 and XP) and a remote site connected via VPN (1x XP PC, also on the same domain as the PCs at the main office).
There are around 10 security groups on our domain, used to provide domain users with access to various network drives. At the main office everything works as expected.
At the remote site, however, some domain users have serious network problems if they are made a member of one particular security group (called "_publicprograms"). Instead of getting more access (as happens at the main site with this security group), they instead cannot view any shares on the server (\\server) if they are a member of this security group.
If the user is then removed from the "_publicprograms" security group, logs out of the PC at the remote site, then back in again, they can once again view and access shares on the server in the normal fashion (both those related to security group and others, such as network printers attached to the server). This issue is 100% repeatable.
This is odd because:
this problem does not happen at the main site with the same domain user account, on PCs in the same OU as the PC at the remote site
there is nothing obviously different about this security group's configuration in AD compared to any of our other security groups
I would not have even thought it possible for security group membership to be able to prevent listing any (or all, in this case) shares on the server in this way. I am not talking just about the user being simply denied access to shares (as could be explained by NTFS permissions)- but being unable to simply list shares on the server.
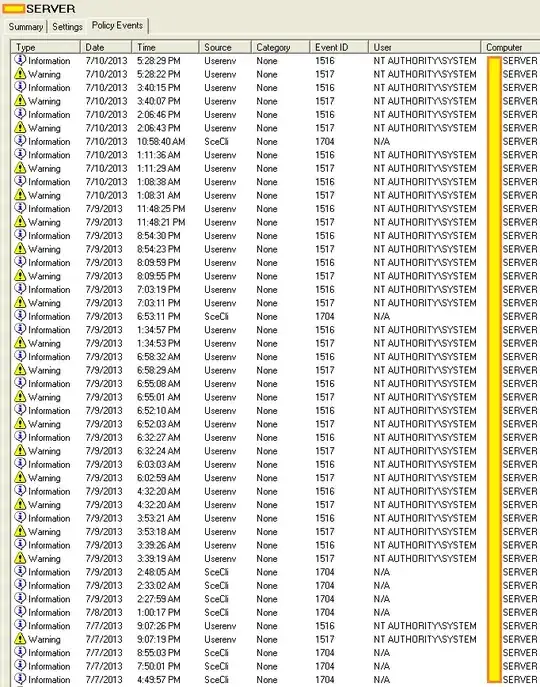
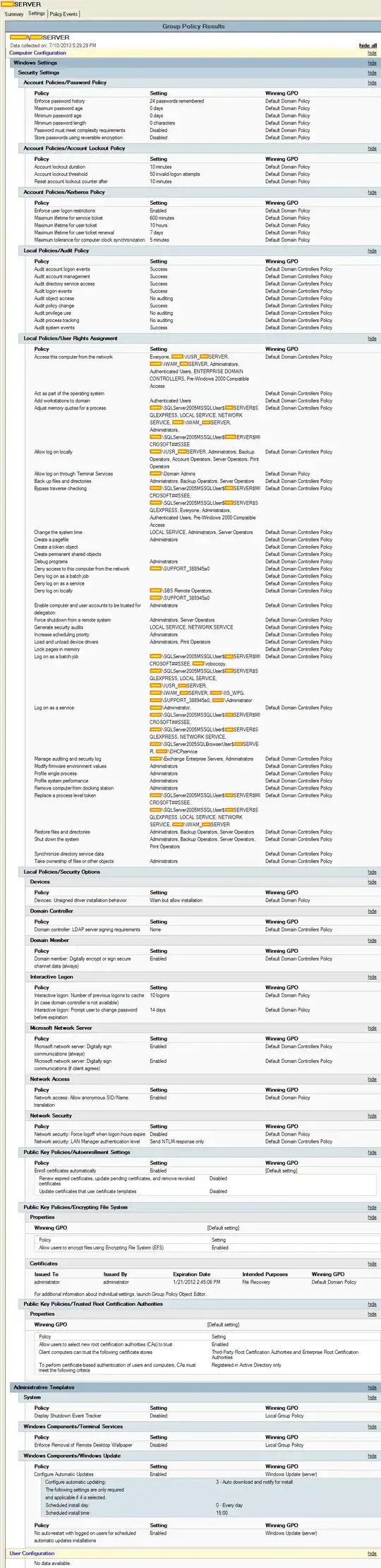
Evan: here is the server's own Resultant Set of Policy as you requested.
Perhaps you will be able to find a clue here:
Summary:

Settings:
Policy Events: