I'm using autossh to open a reverse SSH tunnel using private keys. The tunnel user's shell is rssh and is verified as working.
The problem I'm having is as such, regardless of ClientAliveInterval (15) and ClientAliveCountMax (3) (the sshd defaults), on the client side the tunnel is opened with:
exec autossh -N \
-o "ServerAliveInterval 60" \
-o "ServerAliveCountMax 3" \
-o "StrictHostKeyChecking no" \
-R ${tunnel_port}:localhost:22 \
-i ./tunnel \
-v \
tunnel@directory.mytunnelhost.com
The ${tunnel_port} comes from a small curl call which looks for a free port on the tunnel host, the port doesn't change (it's assigned based on the mac address of the requesting box)
The problem is that when TERMinating the tunnel client, the ports stay occupied on the host, and the sshd process keeps running:
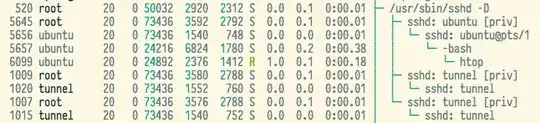
I also can't log into the machines via the tunnel:
ubuntu@ip-10-252-138-233:~$ ssh -p 39777 pi@localhost
ssh: connect to host localhost port 39777: Connection refused
I'm wondering what I can do to make the tunnel more reliable, to make sure when either end goes down that it's completely dead, torn down and can't enter a "broken" state.
If I was tunnelling over port 80 or similar, I could write a check script (this daemon os started with runit) to check that some HTML page was available end-to-end through he tunnel, however when it's over SSH, and as a reverse tunnel, I'm at a loss as to how the client could know if the tunnel is really working as against just running?