I have a custom application that accesses a remote range of IP addresses, lets say for example 206.0.0.0 - 206.255.255.255, this is UDP based traffic. The issue is, Sonicwall NSA has been configured to block all proxy-based access and is detecting this traffic as "PROXY-ACCESS Encrypted Key Exchange -- UDP Random Encryption(UltraSurf) sid=7" and is blocking the application. How would I go about getting this traffic unfiltered access to that ip range? I tried adding address object for that range and creating an access rule to allow it through, but it still seems to be blocked. Any assistance is welcome, thanks.
3 Answers
I was able to allow iOS updates while blocking PROXY-ACCESS. I had to allow HTTP Proxy under PROXY-ACCESS.
- 11
- 1
It would appear (assumption) that the ports you are trying to access externally (maybe 500 or 4500/5500?) are typically reserved for VPN traffic and as such are hitting the block that is setup.
See here: Sonicwall App Control Signature
Basically you'll need to set an exclusion in that block for those external IPs:
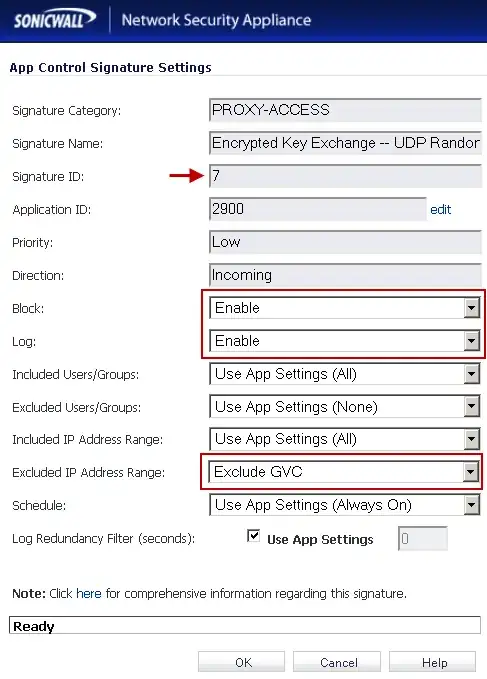
- 32,627
- 26
- 132
- 191
-
Thanks. I have done that but still getting blocked. What Zone should the address object be added to, WAN? – John Jun 10 '13 at 20:17
-
The zone comes into play for allowing outbound access in the policies, yes, but if you haven't changed the signature exclusions then you'll get the exact error you are talking about. Your sure you actualy changed it like in the pic I posted? – TheCleaner Jun 10 '13 at 20:19
-
Yes I changed it as per the picture. I was just curious as to creating the address object for the range of external IP's what zone to put it in, but if that only comes into play ONLY for outbound then this should work, right? I created address object 206.0.0.0 - 206.255.255.255, WAN Zone, then SID7, excluded that address object. – John Jun 10 '13 at 20:22
-
Correct. If you disable the SID7 block and log only does it work ok to test? – TheCleaner Jun 10 '13 at 20:26
-
Yes, disabling SID7 only logs, does not block it. – John Jun 10 '13 at 20:27
Found this in searching for a solution to our problem. We've discovered the same thing. Apple updates for our ipads are being blocked by this same signature. This is the second time we've seen content from Akamai servers blocked for EKE.
At this point, we just opened up all EKE. Just didn't seem worth the hassle to find all the false-positives that this is blocking
- 1