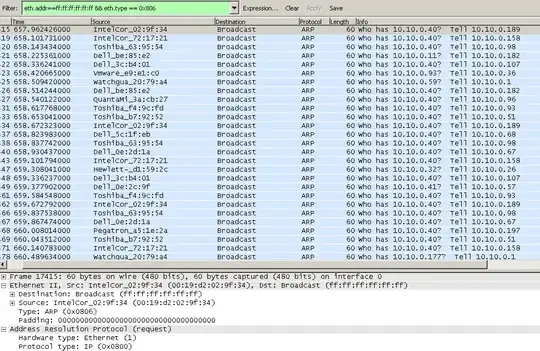
We're seeing some suspicious network activity, and when I was trying to see if it was one particular server of ours I ran a Wireshark trace. I noted a lot of ARP packets asking who has x.x.x.x, but all being told to tell different addresses. In the past I've only seen the "tell" to be a single host - for example a DHCP server.
As you can see from the screenshot, there are only a few IP's being asked for, but the system to tell varies a lot. It's like all devices on the network are trying to find out who 10.10.0.40 (and a couple of others) is.