I am trying to create a simple VPN hub-and-spoke topography. I have managed to get quite a long way and I hope the following diagram describes what I have been able to build thus far:
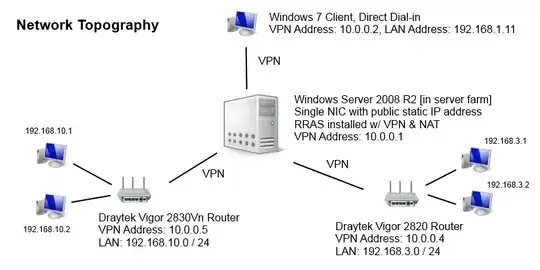
As you can see, the hub is a Windows Server 2008 R2 box running RRAS. The spokes with either be Dreytek routers with a number of PCs (or other devices) on the LAN behind them or PCs dialling in directly to the server. All of this works as expected except for the fact that none of the LAN devices at the spokes are able to communicate with the devices at the other spokes. For example, the direct dial-in PC (192.168.1.11) cannot communicate with 192.168.3.1 or 192.168.10.1.
Things that I have tried and work:
- All of the LAN devices can ping any of VPN addresses (so, for example, the direct dial-in PC can ping 10.0.0.1, 10.0.0.4 and 10.0.0.5).
- I have enabled Syslog on the Draytek routers and can see the ICMP traffic through the firewall when the 10.0.0.x address of the router is pinged (for example, if I ping 10.0.0.5 from the direct dial-in PC, I can see the firewall allowing the ping).
- I have added static routes to the Dreytek routers (for example, on the 10.0.0.5 router, I have added a route for 192.168.1.0 / 24 and 192.168.3.0 / 24 routing via 10.0.0.1).
- I have added static routes to the direct dial-in PC for 192.168.3.0 / 24 via 10.0.0.4 and 192.168.10.0 / 24 via 10.0.0.5
- I have added static routes to the server for each LAN at the end of the spokes (for example, I added a route for 192.168.1.0 / 24 to route via 10.0.0.2, and 192.168.10.0 / 24 via 10.0.0.5). I am having trouble persisting these routes so that they re-establish if the VPN connection drops and re-connects.
Things that don't work:
- The server is unable to ping any of the LAN PCs (for example, it can't ping 192.168.10.1 or .2 etc.). Syslog on the routers does not see any ICMP traffic.
- The client PCs are unable to ping any remote PCs (for example, 192.168.10.x PCs cannot ping 192.168.3.x PCs or the direct dial-in client at 192.168.1.11).
If a use tracert or pathping, it does look like the traffic is trying to go via the server but it never gets there. For example:
C:\Users\Administrator>pathping -n 192.168.10.2
Tracing route to 192.168.10.2 over a maximum of 30 hops
0 10.0.0.1
1 10.0.0.5
2 * * *
I am really at a loss as to what to do next. It must be possible to get this working... I have found so many articles about this topic but nothing seems to address this particular problem. So I guess my two main questions are:
- What am I missing to get the remote LAN PCs to be able to communicate with each other?
- What do I need to do to persist the routes via the VPN clients to their LANs?
- Can I avoid static routes completely and use dynamic routes? I have tried using RIP but the RIP multicasts come in over the VPN (I have seen this using Wireshark) and I can't create RIP on the "Internal Interface".
One idea that I've had... Could the problem be anything to do with IPv6? When I was experimenting, I tried disabling it using Microsoft Fixit 50409. After I did this, neither the routers nor the direct dial-in W7 client were able to establish a VPN connection until I re-enable it... I had assumed that all traffic would be IPv4 but perhaps I'm wrong?
Many thanks!
Edit: In response to Stephane's comment, here are the routing tables for the various components in the network...
Server:
C:\Users\Administrator>route print -4
===========================================================================
Interface List
18...........................RAS (Dial In) Interface
11...00 15 5d 2f 4d 2d ......Microsoft Virtual Machine Bus Network Adapter
1...........................Software Loopback Interface 1
===========================================================================
IPv4 Route Table
===========================================================================
Active Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 109.228.20.1 109.228.20.174 6
10.0.0.1 255.255.255.255 On-link 10.0.0.1 276
10.0.0.2 255.255.255.255 10.0.0.2 10.0.0.1 21
10.0.0.4 255.255.255.255 10.0.0.4 10.0.0.1 21
10.0.0.5 255.255.255.255 10.0.0.5 10.0.0.1 21
109.228.20.0 255.255.252.0 On-link 109.228.20.174 261
109.228.20.174 255.255.255.255 On-link 109.228.20.174 261
109.228.23.255 255.255.255.255 On-link 109.228.20.174 261
127.0.0.0 255.0.0.0 On-link 127.0.0.1 306
127.0.0.1 255.255.255.255 On-link 127.0.0.1 306
127.255.255.255 255.255.255.255 On-link 127.0.0.1 306
192.168.1.11 255.255.255.255 10.0.0.2 10.0.0.1 21
192.168.3.0 255.255.255.0 10.0.0.4 10.0.0.1 21
192.168.10.0 255.255.255.0 10.0.0.5 10.0.0.1 21
224.0.0.0 240.0.0.0 On-link 127.0.0.1 306
224.0.0.0 240.0.0.0 On-link 109.228.20.174 261
224.0.0.0 240.0.0.0 On-link 10.0.0.1 276
255.255.255.255 255.255.255.255 On-link 127.0.0.1 306
255.255.255.255 255.255.255.255 On-link 109.228.20.174 261
255.255.255.255 255.255.255.255 On-link 10.0.0.1 276
===========================================================================
Persistent Routes:
Network Address Netmask Gateway Address Metric
0.0.0.0 0.0.0.0 109.228.20.1 1
===========================================================================
Note: One of the problems I have is that I have to manually add the routes for 192.168.1.11, 192.168.3.0/24 and 192.168.10.0/24 every time the VPN clients connect. This is clearly a serious problem as I have to be able to persist these routes, but maybe it's not possible?
Windows 7 Client:
C:\Windows\system32>route print -4
===========================================================================
Interface List
26...........................CodeArt Consulting VPN
17...90 b1 1c 67 94 d4 ......Realtek PCIe GBE Family Controller
13...68 94 23 36 83 ba ......Bluetooth Device (Personal Area Network)
1...........................Software Loopback Interface 1
11...00 00 00 00 00 00 00 e0 Microsoft ISATAP Adapter
16...00 00 00 00 00 00 00 e0 Microsoft ISATAP Adapter #2
15...00 00 00 00 00 00 00 e0 Teredo Tunneling Pseudo-Interface
18...00 00 00 00 00 00 00 e0 Microsoft ISATAP Adapter #3
===========================================================================
IPv4 Route Table
===========================================================================
Active Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 192.168.1.1 192.168.1.11 10
10.0.0.0 255.0.0.0 10.0.0.1 10.0.0.2 11
10.0.0.2 255.255.255.255 On-link 10.0.0.2 266
109.228.20.174 255.255.255.255 192.168.1.1 192.168.1.11 11
127.0.0.0 255.0.0.0 On-link 127.0.0.1 306
127.0.0.1 255.255.255.255 On-link 127.0.0.1 306
127.255.255.255 255.255.255.255 On-link 127.0.0.1 306
192.168.1.0 255.255.255.0 On-link 192.168.1.11 266
192.168.1.11 255.255.255.255 On-link 192.168.1.11 266
192.168.1.255 255.255.255.255 On-link 192.168.1.11 266
192.168.3.0 255.255.255.0 10.0.0.1 10.0.0.2 11
192.168.10.0 255.255.255.0 10.0.0.1 10.0.0.2 11
224.0.0.0 240.0.0.0 On-link 127.0.0.1 306
224.0.0.0 240.0.0.0 On-link 192.168.1.11 266
224.0.0.0 240.0.0.0 On-link 10.0.0.2 266
255.255.255.255 255.255.255.255 On-link 127.0.0.1 306
255.255.255.255 255.255.255.255 On-link 192.168.1.11 266
255.255.255.255 255.255.255.255 On-link 10.0.0.2 266
===========================================================================
Persistent Routes:
None
Note: I have added the routers to 192.168.3.0/24 and 192.168.10.0/24 manually.
Router 10.0.0.5 / 192.168.10.0/24:
Key: C - connected, S - static, R - RIP, * - default, ~ - private
* 0.0.0.0/ 0.0.0.0 via 188.30.37.17 WAN2
C 10.0.0.1/ 255.255.255.255 directly connected VPN-1
S 10.0.0.0/ 255.255.255.0 via 10.0.0.1 VPN-1
C~ 192.168.10.0/ 255.255.255.0 directly connected LAN
S 192.168.1.0/ 255.255.255.0 via 10.0.0.1 VPN-1
S 192.168.3.0/ 255.255.255.0 via 10.0.0.1 VPN-1
S 188.30.37.17/ 255.255.255.255 via 188.30.37.17 WAN2
Note: The static routes to 192.168.1.0/24 and 192.168.3.0/24 have been added to the router and are persisted as expected.
As far as I can tell, all of the routes are in place correctly but of course, there may be a mistake or something is missing...