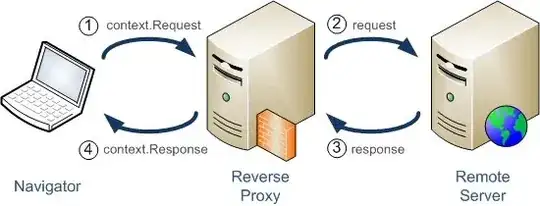
Something like:
ssh -o ProxyCommand="ssh -e none userA@serverA:2000 nc -w 1 serverB 22" userB@ServerB
where you connect to serverA with ssh login userA for opening a forward connection to serverB to wich you log in with userB.
Explanation:
The proxy command open a ssh connection to ServerA (with username userA) and initiate a bidirectional connection to port 22 of serverB.
The initial ssh command use this ProxyCommand to establish a bidirectional connection to ServerB where you have to log in with userB.
In fine:
There is a crypted connection from Laptop to ServerA (step 1 in your drawing) and
another crypted connection from Laptop to ServerB (step 1 + step 2), encapsulated in first connection in his first part (step 1), than binded by nc in the second part (step2).
Instead of HTTP, As SSH is bidirectional, when a connection is open, all requests and answers follow the same connection. So there is no need to think about your step 3 and 4.