I'm trying to find a solution to prevent remote machines determining the source IP of my webserver. This is to hide the webserver's actual IP, helping avoid DDoS attacks.
Incoming requests are already on an HTTP proxy so the IP is not visible for that case, but my outgoing connections (pings & status queries) reveal the source IP to the attacker.
Essentially, I'd like for outgoing TCP and UDP packets to pass through a remote node (which would perform the NAT). The node would then forward the packet with the node's IP and receive any response, which would be passed back to the source machine.
It'd be great if I could specify multiple nodes too, for failover, but I don't know if this is possible.
Apologies if this is using the wrong terminology, my knowledge in this area is somewhat limited.
Edit 1
I have added some example images of what I am trying to achieve.
This is what I currently have, the attacker can trace my source IP from the requests.
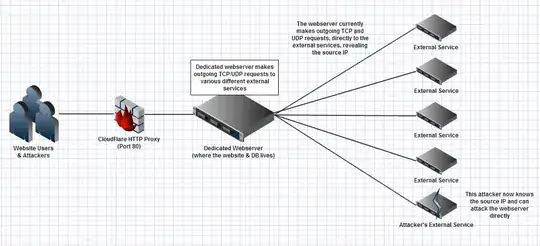 (full size: http://puu.sh/25FNG)
(full size: http://puu.sh/25FNG)
This is what I want to achieve, where the source IP is hidden and if a node is attacked, it does not affect my root server.
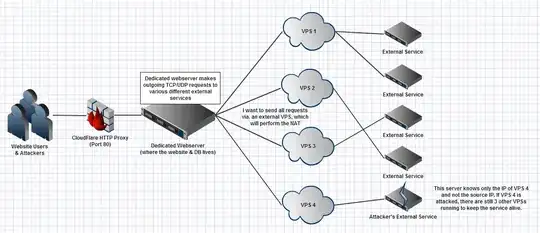 (full size: http://puu.sh/25FR9)
(full size: http://puu.sh/25FR9)