I needed to write a filter that correctly outputs only TCP packets, the obvious way, and the way written in wireshark is just tcp but when I tried it, it showed me also http, tls (as far as I understood everything that relies on TCP).
So my next try was tcp && !http && !ssl which is working correctly. But for sure can show some other protocols that rely on tcp and not included in my ! list.
What is the right way of restricting only to TCP?
Thanks David Schwartz, I really meant packets. The thing, I wanted to achieve - is only to display packets from TCP protocol.
May be I am really not able to express myself. I will try one more time using a picture.
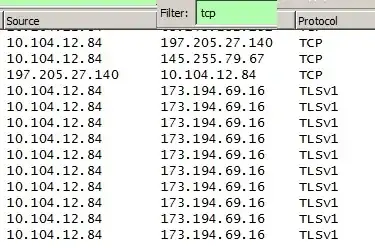
Here is my filter tcp and in the column protocol see tls and something else. I do not want this to happen. So when I am using tcp && !http && !ssl it solves my problem, but can is there anything better?