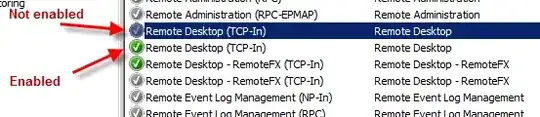
Since people are getting unauthorized access to my Windows Server (bruteforced over several months..), I'd like to set up a whitelist for RDP access.
I have tried the following with Windows Firewall inbound rules:

This still allows other users to connect through RDP. Is there any way to block such unauthorized access through a whitelist?
EDIT: The firewall is enabled, and it's the only firewall running on the machine. Rules like allowing port 80 traffic behave correctly.