The SSL certificate on menswearireland.com and on www.menswearireland.com works fine on Safari, Chrome, SeaMonkey, K-Meleon, QtWeb, Firefox, and Opera. However, Internet Explorer claims that there is an error:
The security certificate presented by this website was not issued by a trusted certificate authority. The security certificate presented by this website was issued for a different website's address.
Security certificate problems may indicate an attempt to fool you or intercept any data you send to the server.
Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.0; Trident/5.0)
Another site hosted on the same managed server shows no errors: achill-fieldschool.com and www.achill-fieldschool.com work fine on IE, even though as far as I can tell the certificate is set up identically.
What am I doing wrong?
This is a LAMPP server running Plesk.
It looks like the server is showing different certificates to different clients. To some clients it shows a RapidSSL certificate made out to www.menswearireland.com with menswearireland.com as a valid alternative name. To other clients, it shows a Parallels Panel certificate, made out to Parallels Panel. Here are results from a few different online SSL checkers: most say it's fine, while two show errors.
Three online checkers say it's valid
Comodo SSL Check shows it as valid
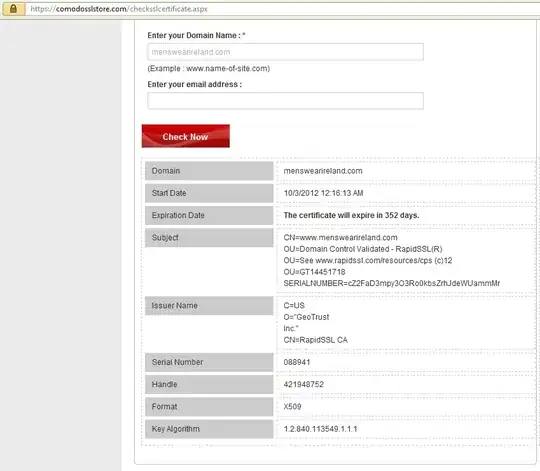
DigiCert SSL Check shows it as valid
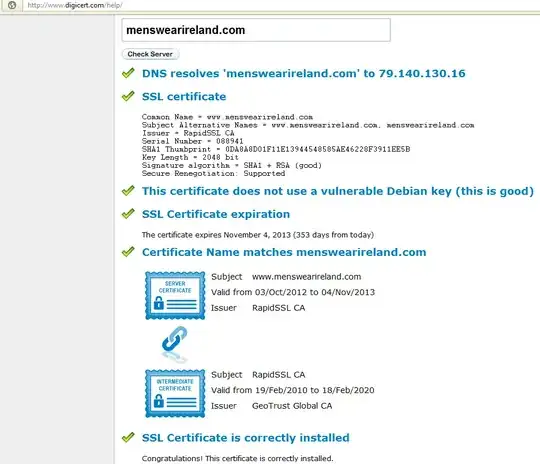
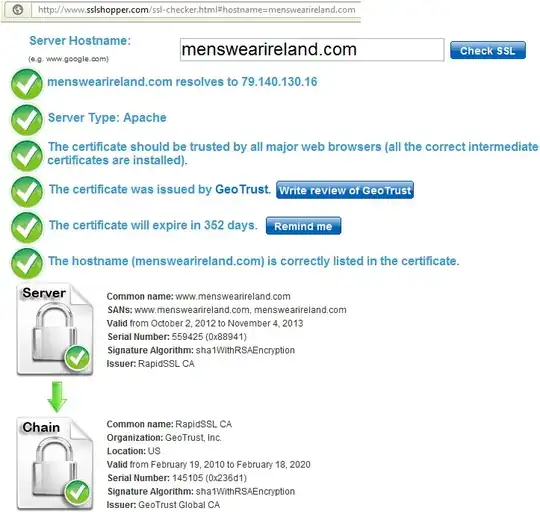
SSL Shopper SSL Check shows it as valid
Common name: www.menswearireland.com
SANs: www.menswearireland.com, menswearireland.com
Valid from October 2, 2012 to November 4, 2013
Serial Number: 559425 (0x88941)
Signature Algorithm: sha1WithRSAEncryption
Issuer: RapidSSL CA
Another online checker seems to see a completely different certificate
GeoCerts SSL Check shows it as invalid
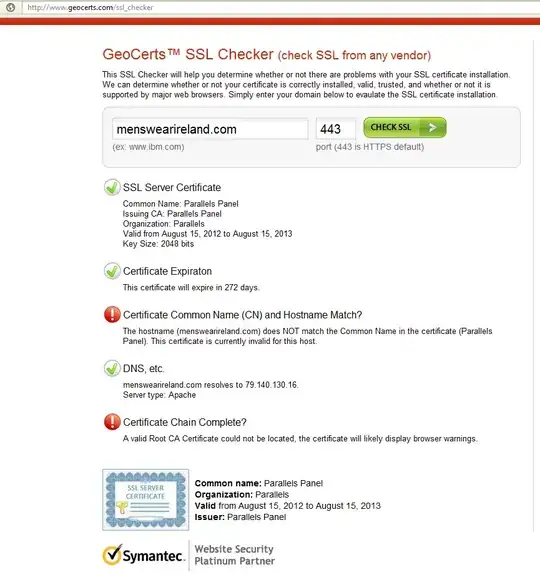
Common name: Parallels Panel
Organization: Parallels
Valid from August 15, 2012 to August 15, 2013
Issuer: Parallels Panel
Another online checker sees more than one certificate
Symantic SSL Check shows it as invalid

The certificate installation checker connected to the Web server and read its certificates, but could not determine which is the primary certificate for the Web server.
Incidentally, on both menswearireland.com and achill-fieldschool.com the homepage will redirect from HTTPS to HTTP. To see SSL details, visit the page /account on both (that page will redirect from HTTP to HTTPS).
I’ve found more information in a more detailed online SSL checker.
https://www.ssllabs.com/ssltest/analyze.html?d=menswearireland.com
This site works only in browsers with SNI support
My understanding is that SNI (RFC 6066) is a method for putting many SSL sites on one shared IP address and port. This does not work on Internet Explorer on older versions of Windows (this has to do with the version of Windows, not the version of Internet Explorer). However, all our SSL sites are on a unique IP address, so we shouldn’t need SNI.