In my org today, we use the following:
- W2K8 R2 - Active Directory
- Google Apps for Enterprise
- Salesforce Enterprise version
Each of these has it's abilities for SSO connectivity. I would like to connect them, so my users will have a single password instead of 3 to remember ( I urge them to replace all 3 every month - they don't listen - I do).
What should be the correct procedure? easiest?
- Google Apps support - SAML, Federated Login with OpenID and 3rd party OAuth. - I can use their google directory sync to sync my domain to the google service.
Salesforce support the following
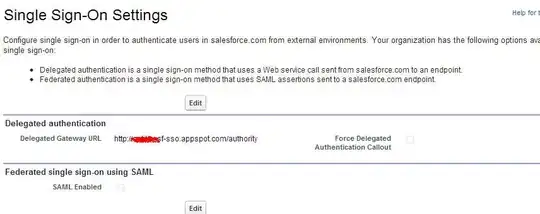
- Where does the Active Directory fit in the picture?
My question is where does SF security fit here? Whom should be the delegate/federated entity? Should I look for a 3rd party? (I think that only adds to the complexity - or not?)
note: I am NOT looking for a step-by-step here. I can't figure the scheme of which entity will hold what position in the SSO authentication process.