We have this topology in our company :
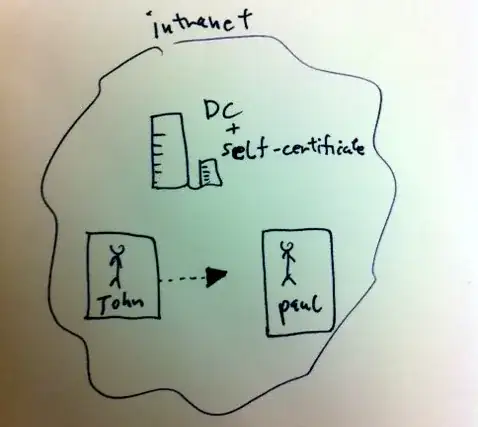
A new rule says that each document being sent by outlook should be encrypted.
we decided using PGP.
We already have a certificate ( self signed).
the problem is this :
john and paul install the certificate .
john encrypt using the public key. and send the pgp file to paul.
paul need the private key in order to open it ( +verify it).
but wait !
private key is private ! and paul should not have access to it.
so how will paul decrpyt john's data ?
What am I missing ?
(p.s. I know I can install pgp as an addon into outlook - but I'm trying to understand the concept of paul not being able to have the private key.)