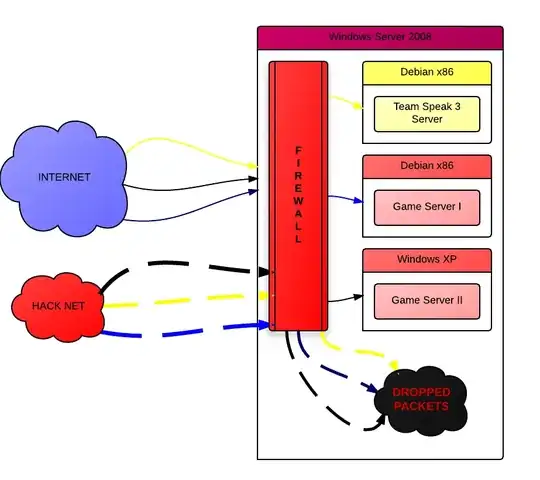
How I can limit UDP/TCP packets per IP send to my host (or better PORT) per second or minute ? Would be nice to ban that IP for 12/24 hours or even for ever.
I got Windows Server 2008 and I'm very poor in Windows administration but quite good in Linux.
EDIT: By basic problem is that They sending a lot of rubbish UPD and TCP packets.. TCP packets without SYNCH, fragmented UDP packets so my servers stop responding..
So I need to cut off users (IPs) sending more than X packets per second. I need solution witch provides me, somehow, configurable: X packets of certain type (UDP, TCP or both - lets say parameter named Z ) are allowed to be received by IP on Y port, otherwise this packet should be DROPPED.
My virtual hosts are hosted by VirtualBox and I'm able to forward all incoming packets certain type and certain port to the specific Virtual Host, but I need to DROP them before my VirtualBox receive them.