Problem
I'd like to enable remote powershell scripting for all workstation hosts on a VLAN. There's no Active Directory or Directory services whatsoever. So HOST A on subnet 192.168.1.x would like to query HOST B 192.168.2.x.
I've already run:
Enable-PSRemoting -force
A prompt for credentials would be the desired result for any workstation on the VLAN. The admin stations are on subnet 192.168.1.x and fall in the IP range 192.168.1.10-20.
Question
Is it possible to allow powershell remote auth for hosts in that range, or any IP coming from a particular subnet?:
192.168.1.0/24
To clarify: I am setting up workstations to deploy and I'd like them to be set up to allow me remote powershell powers out in the field. My admin stations are at one subnet and the workstations to be deployed are at numerous others.
RTFM
I'm looking at this link from Microsoft:
http://technet.microsoft.com/en-us/magazine/ff700227.aspx
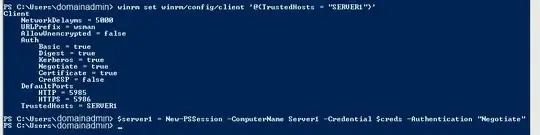
This suggests that I need to run the following for each admin computer:
winrm s winrm/config/client '@{TrustedHosts="RemoteComputer"}'
Can someone confirm or refute this?