So I have a working Active Directory. I've recently added a new machine to act as an Active Directory Certificate Authority.
I've added a Group Policy (Computer level) for automatic certificate enrollment according to this document. And verified that my CA appears in all of my domain members' Trusted Root Certificates.
I've exported the CA's root certificate and added it to my workstation's (computer) Trusted Root CA list.
When I want to remote desktop into my remote servers, it still pops up a warning like this:
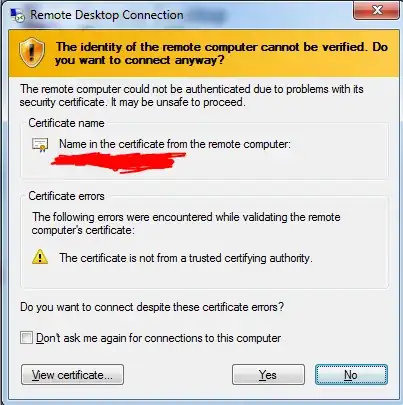
When I view the certificate, it's clear that the certificate that is being sent is the default machine self-signed certificate. How do I get Windows to re-issue machine certificates based on my new trusted root CA? I'm guessing that I need to create an auto-approval policy for machine certificates somewhere with some constraint maybe on who/how such requests can be made. And then I would guess that I need to push a domain policy that somehow instructs all my domain members to get their machine certificate.
Does this sound familiar to anyone? I think the reason I can't find a document on this is because I don't know the correct terminology.