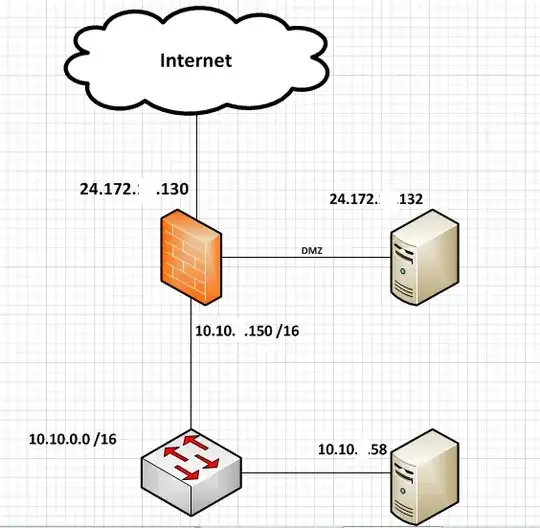
A traditional DMZ would have a firewall between the DMZ and the internet, and one between the DMZ and the inside network. You can do this all on an ASA, but it depends on the model and licensing.
Internet
--------- Firewall
DMZ (with your spam filter)
--------- Firewall
Inside network
You could make that first firewall a software one, running on the spam-filter server.
So you could have the server on the Internet network as far as the ASA is concerned. If you have spare ports on your ASA you could just assign one to the outside network (so you have two) and connect your spam server to that. Then create a firewall rule allowing traffic from the spam-filter server into your inside network as required. If you don't have a spare port, you will need a switch before the ASA.
You could get more fancy using a DMZ vlan on the ASA itself, and use the ASA to firewall the spam-filter, and the inside network. This is probably the closest to what your Sonicwall was doing.