Currently we have a few servers behind a router/gateway, which is in bridge mode, so the servers have directly assigned WAN IPs with no NATting performed. This works as expected.
There is, however a separate office computer network behind a separate gateway, which is connected to the internet via the same router as all the servers.
Here's the simplified scheme: 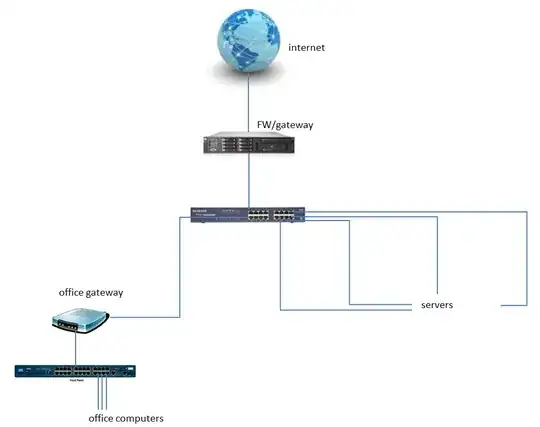
Basically, this means that since the office gateway is connected to the same switch as the servers, they can connect to the servers via their WAN IP without going through the main internet firewall. This is desired and it makes many things easier, however I'm wondering if I should be connecting the servers to the office network separately anyway? It "feels awkward" a little to use the WAN IPs for "internal" communication, but I cannot really think of any big reasons why this would actually be bad...
Thanks