Here is the output of my iptables-save command. The last rule and default policy is to DROP any packets that dont match any thing.
Generated by iptables-save v1.4.9 on Wed Aug 3 21:00:05 2011
*filter
:INPUT DROP [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [76:6239]
-A INPUT -p -m tcp --dport 8080 -j ACCEPT
-A INPUT -p -m tcp --dport 2222 -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -j DROP
But surprisingly, DHCP and every other traffic is getting through... Please advise how to allow connections on port 8080 and port 2222 only and drop everything else.
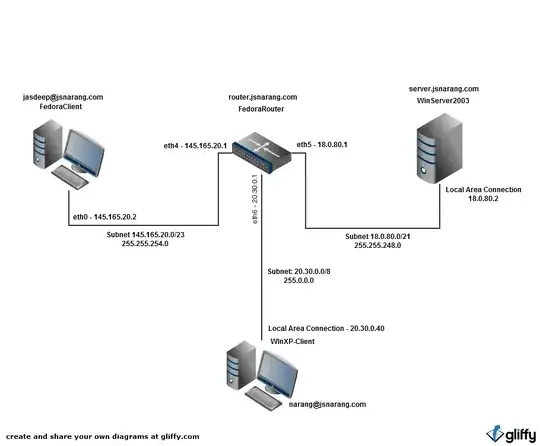
The iptables rules are being set on the FedoraRouter Machine. And this FedoraRouter machine is running Apache and SSH on port 8080 and 2222 respectively.
The clients FedoraClient and WinXP-Client need to have access to these services only. I cannot block them by IP because i'll be adding in more computers in future, anything other than HTTP and SSH traffic needs to be dropped in general.
Based on the current setup - It is allowing DHCP packets to the router, the router is infact running DHCP and i need to block it.
Thanks!