(Updated with config, see bottom).
I've a question regarding the ability of a Cisco ASA 5505 to handle two trunked interfaces when sitting between two switches.
I've gone to the trouble of drawing a diagram to illustrate the setup, as describing it in writing would just be confusing. (The config details have been stripped down for clarity).
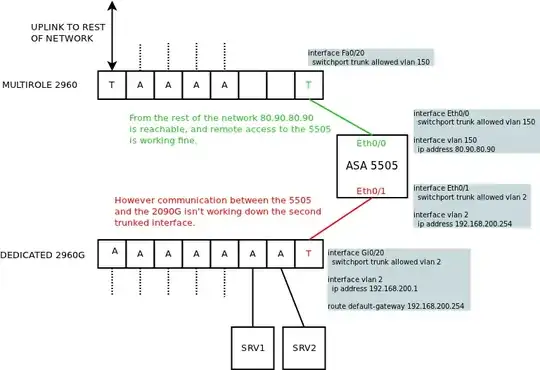
Basically the connection to the ASA 5505 from the rest of the network (via a multirole 2960) is fine. However I'm looking to access a second switch on the other side of the 5505 (which will for the most part be in it's own network).
However when I try and reach the 2960G switch from the firewall I get no response. (Can't ping 192.168.200.254 from the switch, or 192.168.200.1 from the firewall).
I can't get the simplest of connectivity between the firewall's secondary port (Eth0/1) and the 2nd switch. I was hoping to run this connection as a trunked interface so that most machines would be in their own vlan behind the firewall, but in future I could present vlans available to the rest of the network to machines connected to the 2nd switch. However I can't get even basic access to the switch in it's current state.
People have said that they believe a 5505 can't do this as it's a 'glorified switch', but what exactly is stopping it? From my point of view, if a trunked interface works fine on Eth0/0 to access the firewall, why can't I do the same on Eth0/1 so the 2nd switch is accessible from the firewall?
Apologies for the long winded nature of the question, but I am really keen to know if there is something fundamentally wrong in the setup - or if something must just be wrong in the config.
Cheers, Coops.
UPDATE: 5505 config avaliable here: http://pastebin.com/sB7GpqiA Infrastructure IPs / passwords /etc changed for anominity, but the vlans and internal ips should match the diagram. I also added an "allow any any" on all interfaces to rule out firewalling. Vlan1 is also configured, but it's not assigned to anything, it's vlan2 I'm trying to access the switch via.