One of my servers is being flooded with udp packets on random ports.
12:11:54.190442 IP 182.48.38.227.60173 > localhost.51523: UDP, length 1
12:11:54.190447 IP 182.48.38.227.60173 > localhost.23769: UDP, length 1
12:11:54.190560 IP 182.48.38.227.60173 > localhost.4655: UDP, length 1
12:11:54.190564 IP 182.48.38.227.60173 > localhost.13002: UDP, length 1
12:11:54.190685 IP 182.48.38.227.60173 > localhost.52670: UDP, length 1
12:11:54.190690 IP 182.48.38.227.60173 > localhost.21266: UDP, length 1
12:11:54.190696 IP 182.48.38.227.60173 > localhost.7940: UDP, length 1
12:11:54.190810 IP 182.48.38.227.60173 > localhost.35950: UDP, length 1
12:11:54.190818 IP 182.48.38.227.60173 > localhost.62370: UDP, length 1
12:11:54.190828 IP 182.48.38.227.60173 > localhost.28225: UDP, length 1
12:11:54.190935 IP 182.48.38.227.60173 > localhost.56093: UDP, length 1
12:11:54.190939 IP 182.48.38.227.60173 > localhost.54250: UDP, length 1
12:11:54.190941 IP 182.48.38.227.60173 > localhost.15275: UDP, length 1
12:11:54.190948 IP 182.48.38.227.60173 > localhost.28750: UDP, length 1
I've got a lots of these. I know that if system gets an udp packet, it will check if any application want to handle it, if not, it will send a packet back. To prevent this I turned blackholing for udp on.
net.inet.udp.blackhole=1
I must add that I block every attacker with my pf (packet filter) and it seems to help, but he seems to have access to some botnet and changes source IP addresses like I change my socks OR he is just spoofing source ip of packets.
Anyway the attacker is still able to flood my server and I don't know how to defend from it.
I'd appreciate any help.
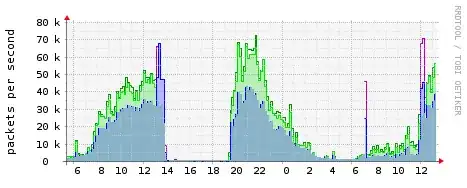
PS. I can't afford a hardware firewall ;)