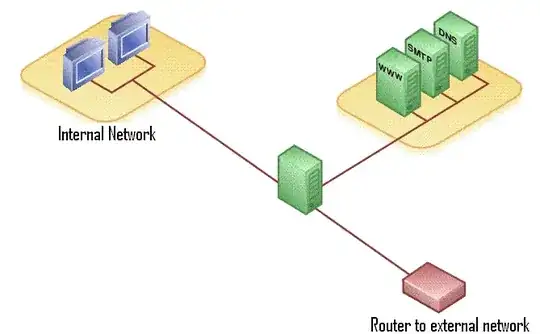
@ooshro gave a good answer about DMZs, but I want to add there are additional steps you should look at for securing your external access to limit the possibility of your host being compromised.
First, make sure you set up proper firewall rules on the linux bugtracker server. Since it will be publically accessible, you should control access in and out of the machine tightly. Most firewall configurations concentrate on blocking incoming connections from the outside world. That's a good first step, but you should also lock down outgoing connections. For example, if this server doesn't need to ssh to the outside world, there should be a firewall rule blocking that.
Install a minimal set of software packages on the server. Do you really need network utilities like tcpdump or traceroute? Probably not, but they can be invaluable for someone who breaks into your machine.
Take additional steps to secure incoming ssh on the linux server. You should run something like denyhosts to block automated login attempts. If only admin users like yourself are going to access the box via ssh, run your ssh server on a different port to again cut down on automated ssh login attempts.
Don't allow password-only ssh logins to the box, instead require use of pregenerated public/private keypairs. Look into running Google Two Factor Authentication so there's an additional layer of security when you log in.