How I do to create a wildcard certificate for ALL domains?
Here is my error:
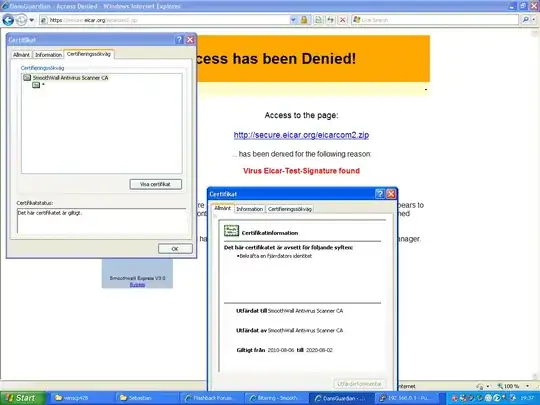
CACERTIFICATE.crt is imported as trusted in my browser. SERVERCERTICIATE.crt and SERVERPRIVATEKEY.key is used in a proxy server which scans SSL traffic for virus.
The problem is that I in IE has to uncheck: "Tools - Internet Options - Advanced - Warn if adresses in certificates does not match*"
for it to not complain about the certificate. (In the picture eicarcert.PNG I have the setting unchecked, and you see that the cert is trusted).
In firefox (latest), I have to click "Add a security exception" for EVERY SSL-site im visiting. Its pretty irritating to have to "Add a security exception" for every SSL site im visiting even if the certificate is trusted.
The firefox pushed out a update to ther SSL handling disallowing * to cover . in domains.
Even having a certificate like *.*.* does not makes the browser trust it.
Is it any way to create a certificate valid for ALL domains over the whole globe?