I have a .net web application which needs to obtain the groups a user is a member of in Active Directory.
Todo this I am using the memberOf attribute on the users records.
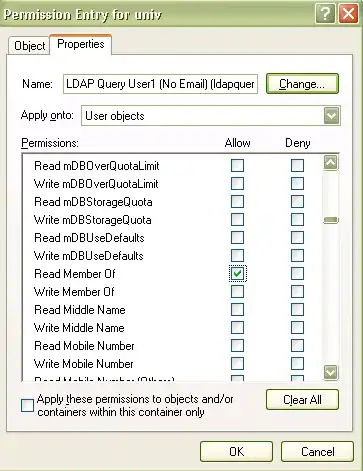
I need to know the permissions required to read this attribute on all users records.
Currently I am getting inconsistent results when trying to read this attribute. For example I have a user group of 30 users in the same OU path. Using my own credentials to query AD - I can read the memberOf attribute for some users but not others. I know all the users have a memberOf attribute set as I have checked when logged on with a domain admin account.