(That public IP belongs to Google, so the edit probably wasn't necessary)
The best thing you can do to secure a SQL server of any stripe is to whitelist the hosts that are allowed to connect to it, and to make sure to run as few other services as possible on that machine.
Another good practice is to severely restrict the access possible from the web side. If the web app is only allowed to run a few dozen stored procedures, then there are practically no attack vectors from an exploited website. On the other hand, if it can run arbitrary queries, then you're going to have problems.
Never run a webserver on your database machine: that's a huge, unnecessary attack vector that should be avoided whenever possible. Webservers and webservices are very often exploited. If your database is attached to the same machine, then it is far more likely to be taken down as well.
The easiest way to achieve all of this (without adding any new hardware) is to enable IPSEC, and tunnel requests from your web server to your database server. Here is a basic IPSEC tutorial.
If you have to have them on the same server, you can get a little security by only allowing local connections, but that's no help if your website gets exploited.
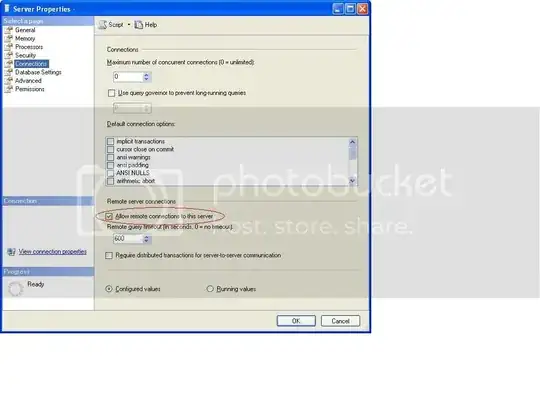
To disable remote connections, go to Server->Properties->Connections and uncheck "Allow Remote Connections to this Server".