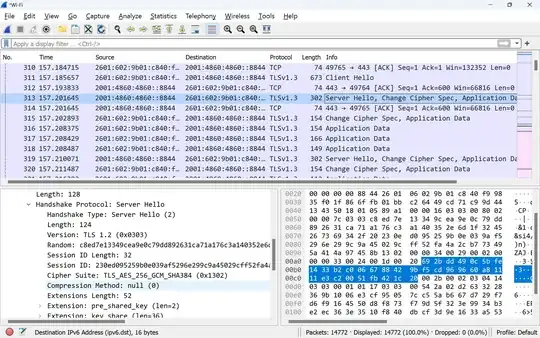
I was browsing Wireshark output and noticed that the handshake process for talking to Google DNS servers was asking for TLS1.2 vs the supported default TLS1.3 at 2001:4860:4860::8844.(https://developers.google.com/speed/public-dns/docs/secure-transports)
How do I set the default TLS version to be used on Windows 11 to TLS1.3 and downgrade to TLS1.2 if that is not available.
Internet Options has TLS 1.2 and TLS 1.3 selected but it seems to default to TLS1.2
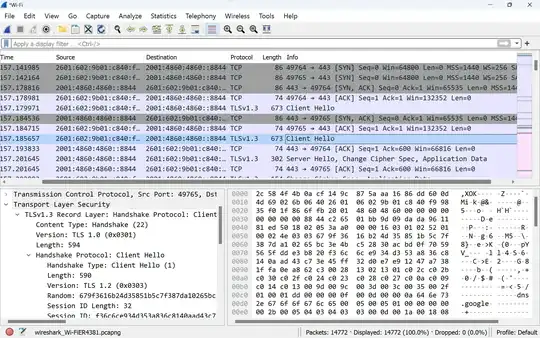
So the client cipher suite supports: TLS_AES_256_GCM_SHA384
And then the server confirms that it supports the same TLS1.3 cipher suite: