I have a deploy-pipeline in Azure devops. I am using this to deploy some objects to our k8s cluster (microk8s). I connect to the cluster with the help of a service connection that uses a kube-config.
Now I want to move to using environments. But when using environments I can't use my service connection nor can I use a kube config, I have to use something called a service account.
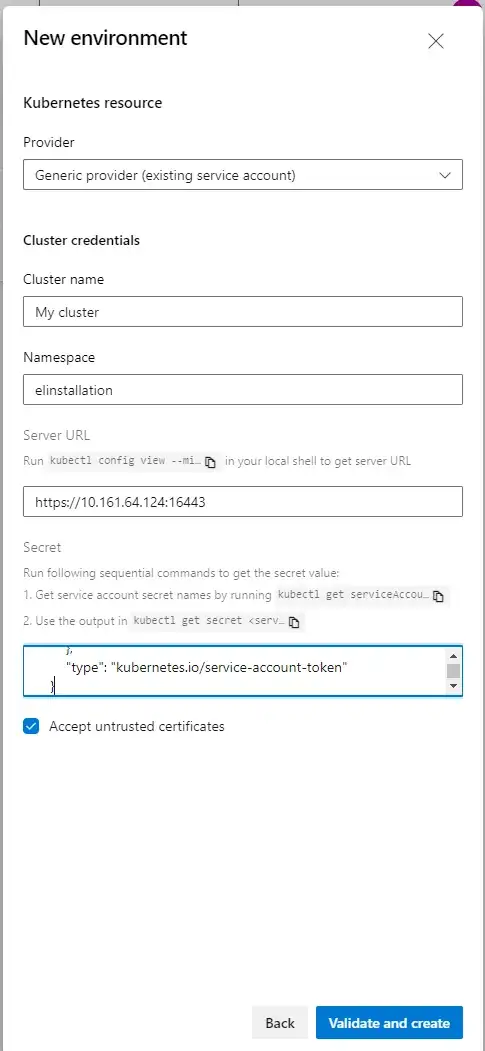
I have tried adding a service account but it fails when trying to connect:
Error from server (BadRequest): the server rejected our request for an unknown reason E0501 20:23:58.096274 11988 request.go:977] Unexpected error when reading response body: read tcp 10.53.225.240:63434->10.161.64.124:16443: wsarecv: An existing connection was forcibly closed by the remote host.
I guess I haven't setup the service account correctly. Here is the yaml for the role, serviceaccount and rolebinding:
apiVersion: v1
kind: ServiceAccount
metadata:
name: app1serviceaccount
namespace: elinstallation
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: elinstallation
name: pod-creator
rules:
- apiGroups: [""]
resources: ["*"]
verbs: ["*"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: pod-creator
namespace: elinstallation
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: pod-creator
subjects:
- kind: ServiceAccount
name: app1serviceaccount
namespace: elinstallation
Also created a secret for the service account:
apiVersion: v1
kind: Secret
metadata:
name: app1serviceaccount-secret
namespace: elinstallation
annotations:
kubernetes.io/service-account.name: app1serviceaccount
type: kubernetes.io/service-account-token
I then copy the output of this command:
kubectl get secret app1serviceaccount-secret -n elinstallation -o json
And paste it into the secret field of the environment. Output looks something like this:
{
"apiVersion": "v1",
"data": {
"ca.crt": "LS0tLxxxxS0tLS0tCg==",
"namespace": "ZWxpbnN0YWxsYXRpb24=",
"token": "ZXlKaGJxxxxx"
},
"kind": "Secret",
"metadata": {
"annotations": {
"kubectl.kubernetes.io/last-applied-configuration": "{\"apiVersion\":\"v1\",\"kind\":\"Secret\",\"metadata\":{\"annotations\":{\"kubernetes.io/service-account.name\":\"app1serviceaccount\"},\"name\":\"app1serviceaccount-secret\",\"namespace\":\"elinstallation\"},\"type\":\"kubernetes.io/service-account-token\"}\n",
"kubernetes.io/service-account.name": "app1serviceaccount",
"kubernetes.io/service-account.uid": "0b62b400-a0a9-4b27-822b-05d12b1c0930"
},
"creationTimestamp": "2023-04-30T07:11:53Z",
"name": "app1serviceaccount-secret",
"namespace": "elinstallation",
"resourceVersion": "12050395",
"uid": "f3b6d9d3-be29-4a85-9ee2-8fe72fca1dd2"
},
"type": "kubernetes.io/service-account-token"
}
One thing that confuses me is that when typing this command:
kubectl get serviceAccounts -n elinstallation
NAME SECRETS AGE
default 0 3d10h
elinstallation-serviceaccount 0 37h
app1serviceaccount 0 36h
test 0 8m46s
It says that no service account has a secret.
What am I doing wrong?
Sub question, is there somewhere in k8s (microk8s) where I can read access logs, to see more details to why I can't connect?