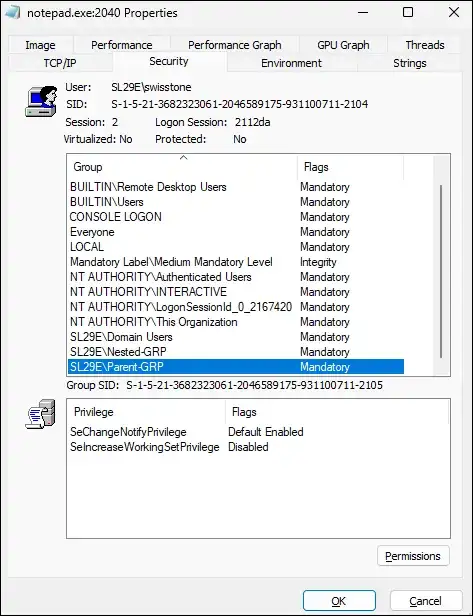
I understand that both NTFS folders and AD objects use security descriptors and DACL’s to check user/process access MS Learn - How access check works
However, how does the access check resolves ACE’s for nested AD groups? For example:
- AD group
AD-Parentis granted Modify rights onF:\Restrict - AD group
AD-VIPsis a child ofAD-Parent - User
vipis a member ofAD-VIPs
My understanding is that
vipsecurity descriptor will have an ACE referring toAD-VIPsandF:RestrictDACL Will have an ACE referring toAD-Parent
How and which process in windows finds the `vip -> AD-VIPs -> AD-Parent’ chain and grants access?