I'm configuring Azure Cloud Service (extended support). Part of the requirements is to apply certain IP security rules, e.g. RDP only from a whitelist of addresses, and some others. With individual VMs, I have used network security groups in the past, however this doesn't seem to work for the cloud service (extended support).
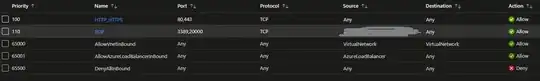
Specifically, I associated a network security group with the subnet in a virtual network, from which role instances get their addresses, yet this NSG's rules don't seem to be adhered to. For example, my inbound rules look like this:
(shaded sources contain allowed 2 IP addresses). Yet I am able to connect to RDP from any other IP address over the internet.
So, the question is how do I apply IP security rules on the cloud service? Whether this is NSG or something else.