I am attempting to force end users onto HTTPS when visiting our site. I have HSTS enabled in IIS at the site and application level. I have an HTTP redirect set up at the site level to https://ourdomain.com. I can visit the home page for our site and see the Strict-Transport-Security: max-age: XXXX; includeSubDomains header, but I am not getting a redirect from http://internal-hostname/ to https://ourdomain.com.
I've read IIS 10.0 Version 1709 HTTP Strict Transport Security (HSTS) Support, and I believe I've followed the steps correctly. After enabling HSTS, I was expecting an automatic redirect from HTTP to HTTPS. I've also read Best way to redirect all HTTP to HTTPS in IIS, but that question focused on IIS7. A lot has changed since then in regard to HSTS support, but maybe my expectations of an automatic redirect are wrong.
System information:
- Windows Server 2019 (version 1809)
- IIS 10.0.17763.1
What I did:
Opened IIS Configuration Manager.
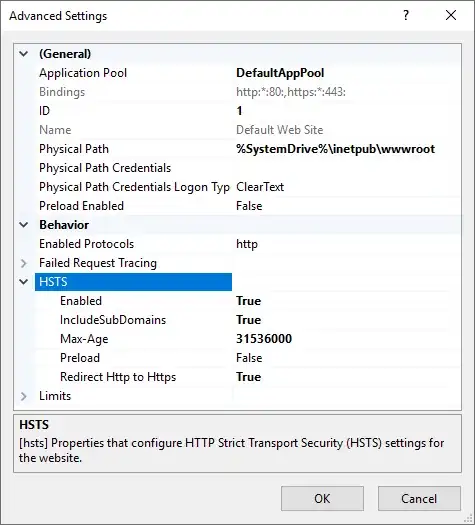
Right-clicked on "Default Web Site", chose "Manage Website" and clicked "Advanced Settings".
Enabled HSTS using the following settings:
- Enabled: True
- IncludeSubDomains: True
- Max-Age: 31536000
- Preload: False
- Redirect HTTP to HTTPS
Clicked "OK"
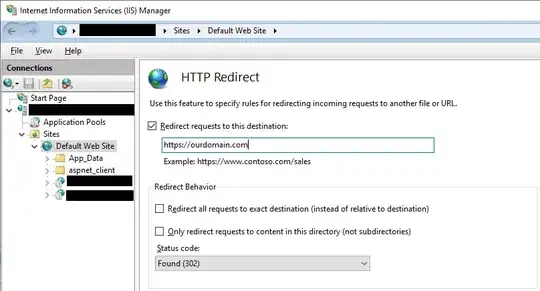
Clicked on "Default Web Site" and chose "HTTP Redirect" under the "IIS" section.
Check marked "Redirect requests to this destination" and entered our HTTPS URL (which happens to be a load balancer, not this particular web server).
Restarted IIS.
While using a remote desktop session to the web server, I opened up Microsoft Edge.
Went to
http://internal-hostname/in Edge.
Expected behavior: the user is redirected to https://ourdomain.com.
Actual behavior: the browser loaded a "403.4 Forbidden" error page.
HSTS seems to be enabled, because I am getting the expected Strict-Transport-Security HTTP header in the response, but I'm not getting the desired redirect from HTTP to HTTPS 1, as specified in RFC 6797.
1 A good answer could also be that "HSTS" is a half-baked solution in IIS 10 and I really do need to add an HTTP redirect rule.