I'm trying to run this command in the AWS console:
aws route53 list-hosted-zones
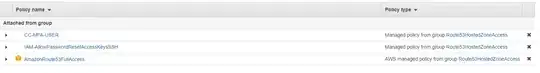
I'm using my access key/secret and it worked fine in a demo account. I checked with my team and I have the AmazongRoute53FullAccess permissions:
Here's the full error message:
PS C:\Users...> aws route53 list-hosted-zones --no-paginate
An error occurred (AccessDenied) when calling the ListHostedZones operation: User: arn:aws:iam::362327418951:user/userName is not authorized to perform: route53:ListHostedZones with an explicit deny in an identity-based policy