I am running into an issue and hoping someone can help me. We were asked to set up a new Root CA and 2 subordinate (issuing) CAs under it (the request includes using Azure and placing each VM in a different region for redundancy). We issued the root, and first subordinate CA, but on the second subordinate CA we are getting 2 errors. -The first is one that we had the option to ignore and did so, it is "Cannot verify certificate chain. Do you wish to ignore the error and continue? The revocation function was unable to check revocation because the revocation server was offline. 0x80092013" -When we clicked ok and ran it anyway, we got "Certutil: -installCert command FAILED: 0x8007139f (WIN32: 5023 ERROR_INVALID_STATE) CertUtil: The group resource is not in the correct state to perform the requested operation." The weird thing is it said everything went well and we just needed to restart for it to take effect and then gave us the second error. All this is in Windows Server 2016 We used this Instruction https://www.derekseaman.com/2021/03/windows-server-2019-two-tier-pki-ca-pt-2.html Part 2 is the part where the issuing CAs start. We followed the same instructions for the second one, but as stated above, it didn't work out.
-
Can all those servers actually connect to each other? Please add some details about your networking. – Massimo Sep 30 '22 at 23:02
-
Is the CRL online? – Greg Askew Oct 01 '22 at 10:33
1 Answers
You should have stopped at the prompt to ignore the certificate verification failure and investigate that. The other errors stem from that problem. Microsoft don't make it clear that it can get messy to continue.
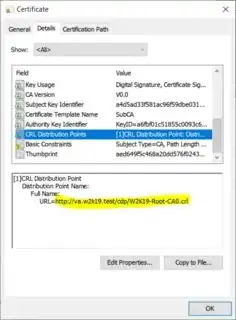
You root CA adds a CRL Distribution Point extension to all certs it issues (the Enterprise CA certs). Look at an issued Enterprise CA cert (with certutil.exe <cert file> or cerutil.exe -UI <cert file>) and find the CRL Distribution Point extension:
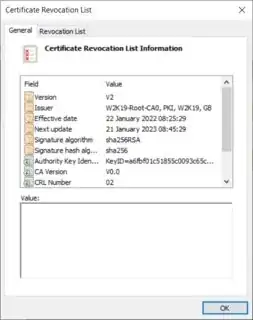
Copy the URL within the CRL Distribution Point extension and attempt to download the CRL (browser or curl.exe). If successful (and you may not be), ensure its valid and issued by the Root CA:
Until you can do that, there is no point continuing with the build. I suspect something went wrong with Part 1 of the article, where you either configure the CRL Distribution Point (with Add-CACRLDistributionPoint) or upload the files to the IIS server.
The Enterprise CA's event logs (Application logs, filter the source to CertificationAuthority) can be useful in these situations.
- 4,539
- 14
- 22