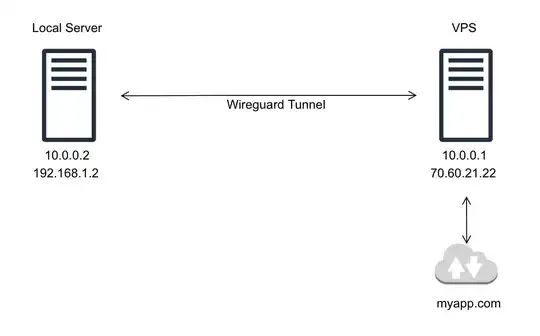
Here is a network topology
The wireguard connection is initiated by the local server, calling the vps through its public IP. Their config files looks like this:
VPS
[Interface]
Address = 10.0.0.1/24
ListenPort = 51820
PrivateKey = ***********************
[Peer]
PublicKey = **************
AllowedIPs = 10.0.0.2/32
Local Server
[Interface]
Address = 10.0.0.2/24
ListenPort = 51820
PrivateKey = ******************
[Peer]
PublicKey = ***************
AllowedIPs = 10.0.0.0/24
Endpoint = 70.60.21.22:51820
PersistentKeepalive = 25
The wireguard tunnel is functional at that point.
The myapp.com domain is pointing to the VPS public IP.
There is a web app sitting in the local server, listening to both HTTP and HTTPS ports. It's got a dynamic IP and is behind NAT. Would be nice to expose it to the public without DDNS or port forwarding. There is a reverse proxy on the VPS that forwards port 80 and 443 packets to it... and it works. Apparently that extra piece of software could be replaced by clever wireguard configs, but that's not our main problem here.
Ok, now, let's say we're developers, so the wording might be a tad incorrect thus far... but thing is, if we tcpdump traffic on the local server while receiving requests from a client pointing to myapp.com, the originating IP always is 10.0.0.1.
For obvious logging and firewalling purposes, we'd prefer to replace this the client's IPs.
What can be done to achieve this?