Hey fellow cloud people,
I am currently experimenting with the new and shiny Update Management Center. As someone having to fiddle around with Update Management in Azure Automation Accounts, I appreciate this new service. Except for assigning VMs to update schedules.
What did I do:
Created a "Maintenance Configuration" with a schedule and update classification (all) for updates
After that, I want to assign machines within a specific scope automatically depending on a tag. We use "UpdateWave" as a tag name. Because I want machines with this tag be onboarded automatically, I need to do that via a policy. Azure calls that procedure "Dynamic scoping" (https://docs.microsoft.com/en-us/azure/update-center/scheduled-patching?tabs=schedule-updates-single-overview%2Cschedule-updates-scale-overview#dynamic-scoping).
I created a policy assignment for "[Preview]: Configure periodic checking for missing system updates on azure virtual machines" which configures machines to automatically check for updates.
When I check the compliance, I see my test machines compliant with that policy after a while.
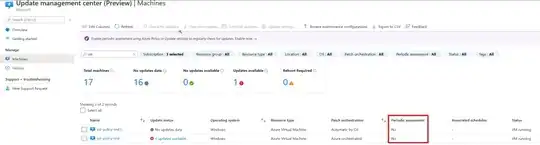
First Problem: But when I look at the Update Management Center, periodic assessment is not enabled.
Does anybody have an idea, what's wrong here? In the mean time, hours went by and its still the same.
Second problem:
After the assessment, I want machines of course assigned to a schedule. This must be done via a policy as well. For that, I assigned the "[Preview] Schedule recurring updates using Update Management Center" policy to the subscription and deployment of the assignment worked. This assignment should basically assign all VMs in the scoped subscription to that schedule (I removed all filtering tags for testing purposes).
When I look at the compliance, I do not get to see any VM. It seems like there are no matching VMs. But the scoped subscription "eu2-iaaststu-sub" indeed has my 2 VMs of OS Windows. I created a remediation task twice (with "Re-evaluate resource compliance before remediating" enabled) and it completed. But it always has 0 affected resources. I don't get it!
I am owner of the target subscription.
I would really love to use the service. It makes it so much easier to onboard machines. IF IT WOULD WORK!
Anybody an idea, what the reasons for both errors are?? Or any other tipps?
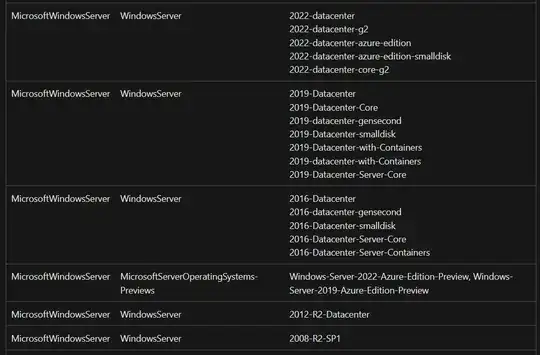
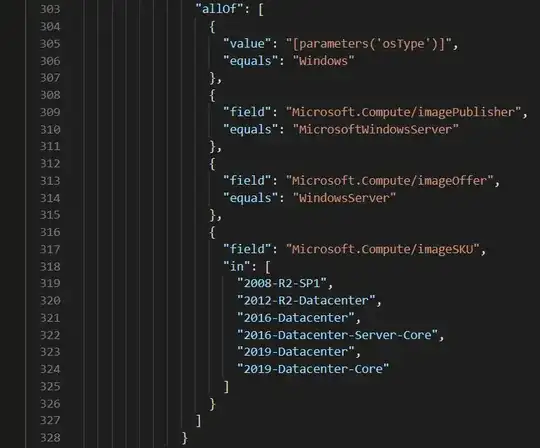
Update 11/07/2022: Microsoft fixed most parts of the policy definitions. The policies now support the operating systems, that support Update Management. Automatic remediation is still not working by now.
[Preview]: Configure periodic checking for missing system updates on azure virtual machines: https://www.azadvertizer.net/azpolicyadvertizer/59efceea-0c96-497e-a4a1-4eb2290dac15.html?desc=compareJson&left=https%3A%2F%2Fwww.azadvertizer.net%2Fazpolicyadvertizerjson%2F59efceea-0c96-497e-a4a1-4eb2290dac15_2.0.0-preview.json&right=https%3A%2F%2Fwww.azadvertizer.net%2Fazpolicyadvertizerjson%2F59efceea-0c96-497e-a4a1-4eb2290dac15_3.0.0-preview.json
[Preview]: Schedule recurring updates using Update Management Center: https://www.azadvertizer.net/azpolicyadvertizer/ba0df93e-e4ac-479a-aac2-134bbae39a1a.html?desc=compareJson&left=https%3A%2F%2Fwww.azadvertizer.net%2Fazpolicyadvertizerjson%2Fba0df93e-e4ac-479a-aac2-134bbae39a1a_1.0.0-preview.json&right=https%3A%2F%2Fwww.azadvertizer.net%2Fazpolicyadvertizerjson%2Fba0df93e-e4ac-479a-aac2-134bbae39a1a_2.0.0-preview.json