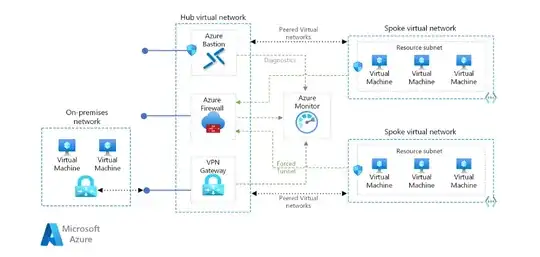
We are developing an app in Azure, made dev/test/prod ressource groups and want to connect these via Site-to-Site VPN to our On-Prem environment. Connecting one of these ressource groups isn't a problem, connecting all of them is unfortunately. We use Sophos XG Firewalls and I set up the connection as described here: https://community.sophos.com/sophos-xg-firewall/f/recommended-reads/126356/sophos-xg-firewall-v18-to-azure-vpn-gateway-ipsec-connection My problem here is step 5/step 8. The vti/xfrm interface gets always the same ip from azure but naturally I can't use the same ip on multiple (virtual) interfaces on my firewall. It's always: int tunnel 11 ip address 169.254.0.1 255.255.255.252
So my question is and I already searched a lot and didn't find anything, am I able to change this IP somehow? Does it even make sense to set up a s2s vpn from every ressource group or would best practice here a different scenario?
I googled up and down but it feels I'm the only one wanting to connect multiple ressource groups to the same on-prem gateway, but that surely can't be right.