EDIT: Solution found. Will post after synthesization and verification.
Having come across some head-scratching behavior with nftables, I am hoping for some community insights.
When using the below ruleset in a QEMU-KVM guest, Ethernet frames in chain arp-out-host-wan0 that nftables should accept are not recognized. Internal nftables logging shows the frames as, from what I can tell, nonsense, while VM guest tcpdump and VM host Wireshark verifies the frames being as expected.
table arp filter {
chain input {
type filter hook input priority filter; policy drop;
iifname "enp1s0" counter packets 5 bytes 140 jump arp-in-host-wan0
log prefix "nft: arp->input dropped: " flags all limit rate 3/second
counter packets 0 bytes 0
}
chain output {
type filter hook output priority filter; policy drop;
oifname "enp1s0" counter packets 5 bytes 210 jump arp-out-host-wan0
log prefix "nft: arp->output dropped: " flags all limit rate 3/second
counter packets 0 bytes 0
}
chain arp-in-host-wan0 {
ether daddr 52:54:00:ee:10:e6 limit rate 3/second counter packets 5 bytes 140 accept
ether daddr ff:ff:ff:ff:ff:ff limit rate 3/second counter packets 0 bytes 0 accept
counter packets 0 bytes 0 return
}
chain arp-out-host-wan0 {
### Broken rule not matching frames that should match
ether saddr 52:54:00:ee:10:e6 limit rate 3/second counter packets 0 bytes 0 accept
### Wildcard rule to log non-matching frames in chain
log prefix "nft: arp->output ALLOWED: " flags all
### Wildcard rule to let non-matching traffic pass
counter packets 5 bytes 210 accept
counter packets 0 bytes 0 return
}
}
QEMU-KVM guest (journalctl -k), traffic as picked up by the above nftables wildcard rule (seemingly nonsense, pay attention to non-standard EthrType, ARP HTYPE, ARP PTYPE, ARP OPCODE):

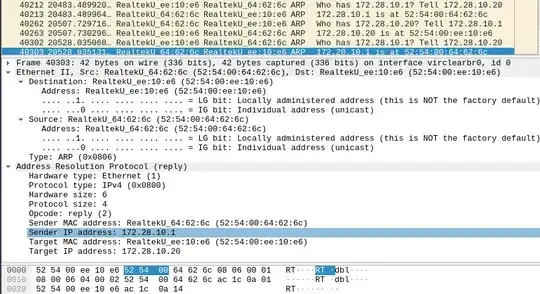
QEMU-KVM guest (tcpdump arp -vlenx), the very same traffic recognized properly:

QEMU-KVM host (Wireshark capture from relevant bridge-device), the very same traffic recognized properly:
I would love to understand what is going on here. If there is any additional info I can provide, just let me know - thanks!
UPDATE 1: Same behavior is observed when logging with NFLOG (syntax "log group").
Frame 1: 76 bytes on wire (608 bits), 76 bytes captured (608 bits) on interface nflog:30, id 0
Interface id: 0 (nflog:30)
Interface name: nflog:30
Encapsulation type: NFLOG (141)
Arrival Time: Jun 28, 2022 09:18:44.633102000 CDT
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1656425924.633102000 seconds
[Time delta from previous captured frame: 0.000000000 seconds]
[Time delta from previous displayed frame: 0.000000000 seconds]
[Time since reference or first frame: 0.000000000 seconds]
Frame Number: 1
Frame Length: 76 bytes (608 bits)
Capture Length: 76 bytes (608 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: nflog:arp]
Linux Netfilter NFLOG
Family: ARP (3)
Version: 0
Resource id: 30
TLV Type: NFULA_PACKET_HDR (1), Length: 8
Length: 8
.000 0000 0000 0001 = Type: NFULA_PACKET_HDR (1)
HW protocol: ARP (0x0806)
Netfilter hook: Local in (1)
TLV Type: NFULA_PREFIX (10), Length: 5
Length: 5
.000 0000 0000 1010 = Type: NFULA_PREFIX (10)
Prefix:
TLV Type: NFULA_IFINDEX_OUTDEV (5), Length: 8
Length: 8
.000 0000 0000 0101 = Type: NFULA_IFINDEX_OUTDEV (5)
IFINDEX_OUTDEV: 2
TLV Type: NFULA_PAYLOAD (9), Length: 46
Length: 46
.000 0000 0000 1001 = Type: NFULA_PAYLOAD (9)
Address Resolution Protocol
Hardware type: Unknown (21076)
Protocol type: Unknown (0x0064)
Hardware size: 98
Protocol size: 108
Opcode: Unknown (21076)
[Malformed Packet: ARP/RARP]
[Expert Info (Error/Malformed): Malformed Packet (Exception occurred)]
[Malformed Packet (Exception occurred)]
[Severity level: Error]
[Group: Malformed]