I have two servers A and B that host websites that work fine in a browser with https. The lock icon in the browsers show active and trusted SSL certificates.
I'm trying to run curl so that server A can talk to server B, but am running into an error.
- Server A -
$ curl https://dev.partsvu.com
CAfile: /etc/pki/tls/certs/ca-bundle.crt
curl: (60) Peer's Certificate issuer is not recognized.
I've done some research around the Stack Overflow sites and have run into many questions, however, their solutions haven't worked for me.
I first tried downloading the certificates files for server B from an SSL Labs report and manually added the list of certificates to the /etc/pki/tls/certs/ca-bundle.crt file on server A but I'm still getting the same error.
I've also ensured that the server B certificate is valid with the following:
- Server B -
openssl x509 -dates -noout < /etc/pki/tls/certs/cloudflare.pem
notBefore=May 6 21:25:00 2022 GMT
notAfter=May 2 21:25:00 2037 GMT
I've also tried copying the contents of /etc/pki/tls/certs/cloudflare.pem on server B directly to the /etc/pki/tls/certs/ca-bundle.crt on server A but same error.
Lastly, I tried visiting server B in Chrome and downloaded the crt file it shows at https://cacerts.digicert.com/CloudflareIncECCCA-3.crt, converted it to pem with:
openssl x509 -inform DES -in CloudflareIncECCCA-3.crt -out outcert.pem
and added that to the same ca-bundle.crt file on server A.
Same error when trying to run curl.
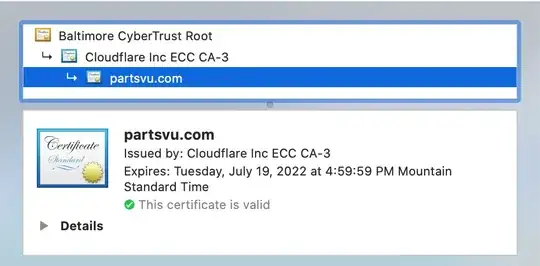
Here is the cert chain from Chrome: