I have a certificate template (auto-enrolled) that must require manager approval.
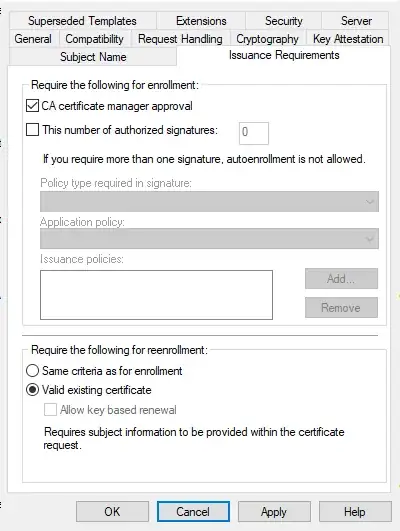
To achieve this, I checked the CA certificate manager approval checkbox in the Issuance Requirements tab.
The computer does auto-enroll and the certificate is placed on the Pending queue on the CA.
My wish is that once the pending certificate was manually approved, certificates should be renewed, or updated if the template major version increments, without manager approval. But I can't get this to work.
When I increment the major version of the certificate, the request is never automatically issued, but again put into the Pending queue for manual issuance.
I tried changing the Same criteria as for enrollment to Valid existing certificate but this didn't change anything.
To speed up my troubleshooting, I used certutil -pulse to start the auto-enrollment process on the requesting computer.
Edit:
The auto-enrollment policy on the affected server: