I've got a running OpenVPN server with following configuration
- VPN network is 10.7.0.0/16
- LAN network is 192.168.100.0/24
Client is able to connect, but I can not reach LAN hosts located behind VPN connection (192.168.100.*).
push "route 192.168.100.0 255.255.255.0" configuration line should solve this, but not. Where is my error ?
Analysis
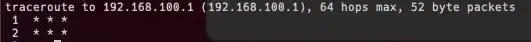
After connection, here is my
netstat -rnresult
default 10.7.0.5 UGScIg utun10
10.7/16 10.7.0.5 UGSc utun10
10.7.0.5 10.7.0.6 UHr utun10
10.7.0.5/32 link#23 UCS utun10
192.168.100 10.7.0.5 UGSc utun10
I would have expected
10.7.0.1gateway on last line, no ?
ifconfig Maybe a clue, my
ifconfigon client gives meI expected something like
inet 10.7.0.2 --> 10.7.0.1as it works on other VPN I got on other context.
↳ Answered with @lacek answer.
Packets Capture
A tcpdump on VPN server, during client pings, gives me
If I capture any ICMP traffic on target, there is no log about ping request. (I've tried from another LAN host, it works. From VPN host directly, it also works.).
The point is that OpenVPN service do not forward my packets to LAN network.
Config
server.conf conf
proto udp
ifconfig-pool-persist ipp.txt
keepalive 10 120
user nobody
group nogroup
persist-key
persist-tun
status /var/log/openvpn.log
verb 3
mute 10
ca /etc/openvpn/server/ca.crt
cert /etc/openvpn/server/server.crt
key /etc/openvpn/server/server.key
dh /etc/openvpn/server/dh.pem
port 1194
dev tun
server 10.7.0.0 255.255.255.0
push "dhcp-option DNS 8.8.8.8"
push "dhcp-option DNS 8.8.4.4"
push "route 192.168.100.0 255.255.255.0 "
client-to-client
On server side, I'm running OpenVPN 2.4.0 on Debian OS.