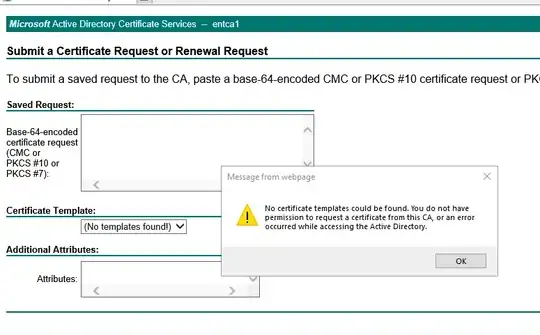
There are a lot of discussions on here about this problem, and I have spent all day exploring every one of them. All the servers involved in this are Windows 2019. 2 domain controllers and a certificate authority server. After installing the Certificate Services feature, I then also installed the Web Enrollment stuff. But when I go to my server's enrollment site, I am greeted with this error:
I've chased down several options. I validated permissions via: https://www.altaro.com/hyper-v/windows-ssl-certificate-templates/
I verified LDAP object configurations via: https://docs.microsoft.com/en-US/troubleshoot/windows-server/windows-security/no-certificate-templates-be-found
I verified the configuration from this site: https://docs.microsoft.com/en-us/answers/questions/96739/certificate-template-not-showing.html
I'm running out of options. The template is clearly there:
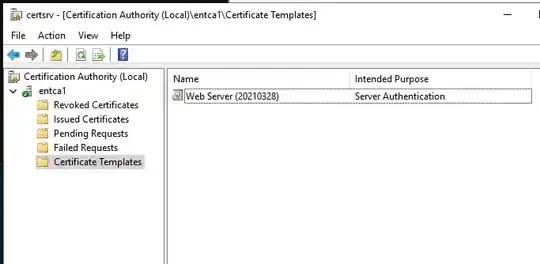
I'm completely out of ideas. I'm frustrated by this. Has anyone got any other ideas?