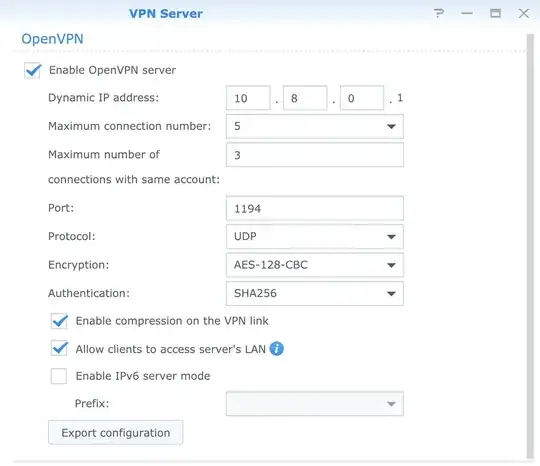
I followed official Synology documentation and I created an OpenVPN Server to connect remotely to a NAS, that is in a LAN with its NAS_LOCAL_IP_ADDRESS. The VPN server configuration is like the following one:
Now, I'm trying to connect from my Mac via Tunnelblick following their instructions. In particular, they say:
Open the exported file openvpn.ovpn with TextEdit and replace YOUR_SERVER_IP with the public IP address of your Synology NAS. If you wish to send all traffic over VPN, remove # from #redirect-gateway def1.
Here is my VPNConfig.ovpn:
dev tun
tls-client
remote YOUR_SERVER_IP 1194
pull
# If you want to connect by Server's IPv6 address, you should use
# "proto udp6" in UDP mode or "proto tcp6-client" in TCP mode
proto udp
script-security 2
comp-lzo
reneg-sec 0
cipher AES-256-CBC
auth SHA512
auth-user-pass
I do not want to reroute all the traffic to the VPN, I just wanna route requests to my NAS_LOCAL_IP_ADDRESS.
If I leave #redirect-gateway def1 commented, the VPN seems working this way. This is what I want but I cannot understand why it happens, since I've never specified the NAS_LOCAL_IP_ADDRESS anywhere in the config file.
Can you folks help me understand how things work under the hood?