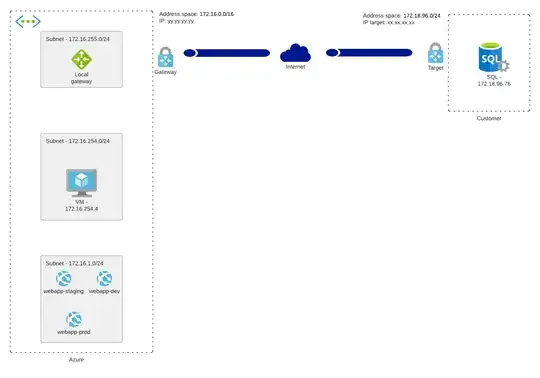
I have this setup in Azure:
- A vnet with address space: 172.16.0.0/16
- A subnet with 172.16.1.0/24 named WebAppSubnet and delegated ot Microsoft.Web/serverFarms
- A subnet with 172.16.255.0/24 named GatewaySubnet
- A local gateway with address space 172.18.96.76/32
- A public Ip associated with the gateway
- A connection, configured with a custom config
- IKE Phase 1 with AES256, SHA256 and DHG 1
- IKE Phase 2 (IPSec) with AES256, SHA256 and No PF Group
- IPsec SA lifetime in KiloBytes set to 102400000
- IPsec SA lifetime in seconds set to 28800
- disabled traffic selector
- DPD timeout set to 45
- BGP and Azure private IP is disabled
- IKE protocol is IKEv2
- A virtual gateway, provisioned into the GatewaySubnet, connected with the local gateway and the connection
- No point to site enabled
All resources is located in West Europe and in the same resource group.
The connection is reporting "Connected", and the onprem IT guys can also see that it is connected.
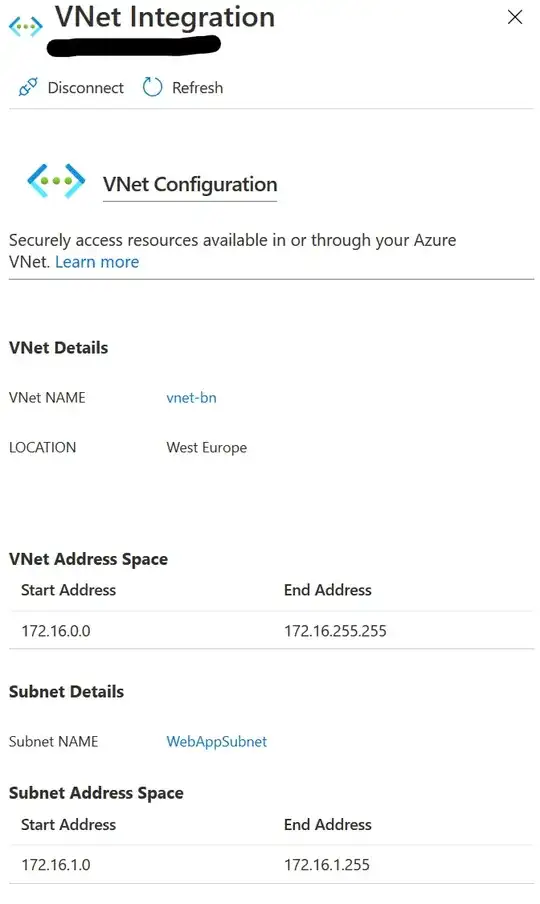
I want to connect one webapp to the VNET so it can connect to the onprem SQL server located at 172.18.96.76. Therefore i check to see if the webapp is added correctly to the VNET:
This is perfect. It works: the webapp is in the VNET. Now i want to point my connection string to onprem SQL. I use this connection string
Server=172.18.96.76;Database=AutodesktopMirror;User Id=myuser;Password=mypass;
but I get an error telling me:
Win32Exception: Access is denied.
Unknown location
SqlException: A network-related or instance-specific error occurred while establishing a connection to SQL Server. The server was not found or was not accessible. Verify that the instance name is correct and that SQL Server is configured to allow remote connections. (provider: Named Pipes Provider, error: 40 - Could not open a connection to SQL Server)
So, it doesn't locate the onprem SQL server, and this is where i gets a bit tricky, because:
- i can't ping the gateway
- i can't do tracert from the webapp
I haven't added WEBSITE_VNET_ROUTE_ALL to the webapp settings. I have tested with and without it, and it gives me the same results: Access Denied, Unknown location.
So basically i don't really know if my traffic gets routed properly. All i know is that all RFC1918 traffic gets routed to the VNET. My webapp is in the VNET, my gateway is in the VNET. What i can see is that no traffic hits the gateway, if i look at the network graphs:
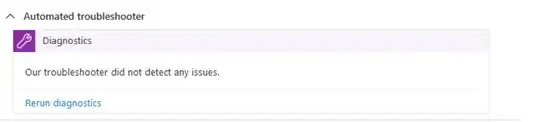
and I have set health probes up to ping the SQL server every two minutes + i have tried all sorts of calls. I have also tried to troubleshot the connectivity on the VPN gateway, and it tells me:
I have googled my a** of, and I have so confused by the mix of "classic VNETs/point-to-site vs no point-to-site". Someone here on serverfault even states that it should just work: https://serverfault.com/a/1046325/133202, because when my webapp is on the VNET with the gateway, it should be able to call through to the onprem database.
Am i missing something in my setup? I have no point to site, should I have? I am happy if i can just get confirmation on if my Azure setup is ok, with the VNET, gateway and IP ranges, because then i think i am going to look more into how the onprem is connected. Maybe they need to update something on their side.
I am not a network administrator, so i am a bit left in the dark when it comes to VPN setup.
All this is provisioned with ARM.
UPDATED
Customer end VPN: Fortigate FortiOS 6.2
Solution
- you dont need site to site if the VNET and webapps is in same region. If the gateway is in the VNET, and the connection is working, all traffic is guided through this
- Remember that only all RFC1918 traffic is routed to the VNET pr default
- you need to setup the gateway as described here: https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-diagnose-on-premises-connectivity#scenario
- Check your firewall rules :) And then check them again
- this just works, if you set a VNET up, with a GatewaySubnet, and a WebAppSubnet and have the local gateway correctly mapped to the onprem address space configured in the onprem gateway. YOU DONT NEED: point-to-site on the gateway, or WEBSITE_VNET_ROUTE_ALL in the webapp config (if you follow the RFC1918 address spacing)
Massive thanks to Massimo, https://serverfault.com/users/6352/massimo!!