Our Cisco Umbrella service is identifying DNS requests to rev1.globalrootservers.net and rev2.globalrootservers.net as malicious. I am trying to figure out whether this is really a problem or if it is a false positive. Below is all the troubleshooting I have performed.
The sole indicators of maliciousness are OpenDNS stating the globalrootservers.net domain is malware and VirusTotal-Fortinet is reporting malware as well for the rev2.globalrootservers.net. All pointers for the rev1 and rev2 DNS names currently point to 0.0.0.0 as the IP.
The otx.alienvault.com passive DNS entries for globalrootservers.net (Figure 3) change from time to time and IPs resolve to various non-reputable domains.
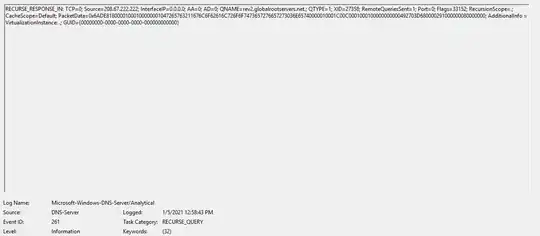
Since we do not have the Umbrella VA deployed, I cleared the cache and turned on DNS logging on both domain controllers. I caught evidence of the DNS hit from only the 2016 domain controller. After capturing the request and response (Figures 1 and 2) multiple times over many days, it never came from the 2012 domain controller. It looks like the source is our 2016 domain controller and I can’t figure out why this is. I have included the entries below if anyone can tell me this is correct.
Figure 1: DNS Request
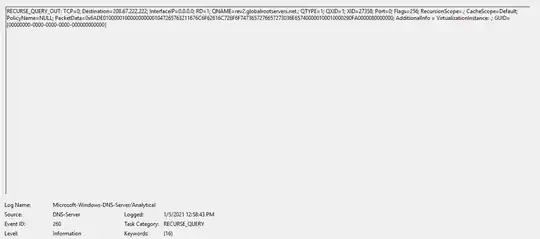
Figure 2: DNS Response
I then go to the 2016 Domain Controller cache and look at the entries. The entries from the in-addr folder are below. Can someone help me in understanding what this means?
Since the rev1.globalrootservers.net and rev2.globalrootservers.net entries are the child of the DNS parents (which indicate afrinic.net, lacnic.net, apnic.net, ripe.net and arin.net), is this nothing to worry about?
Figure 3:Parent cache entry
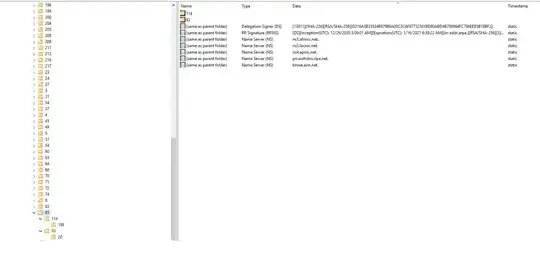
Figure 4:Rev1 and Rev2 child entries
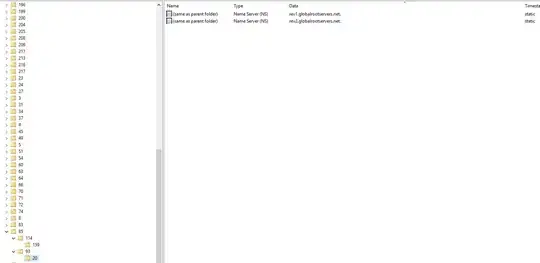
Figure 5: Properties of rev1 and rev2
Furthermore, when looking up the IP address located in the properties of the rev1 and rev2 cache, it points to Microsoft which is a Azure SQL Managed Instance within the 20.64.0.0/10 IP range.
I would greatly appreciate any assistance in identifying if this is a real problem, a solution or to further my troubleshooting. Thank you!