I'm a teacher and I want to simulate with my students a MITM attack. The goal is to show why the https protocol must be always used.
On debian, I installed tshark. All works fine, when I run the hotspot mode and run tshark, I can get HTTP packets and, digging a little, we can see the form datas in plain text :
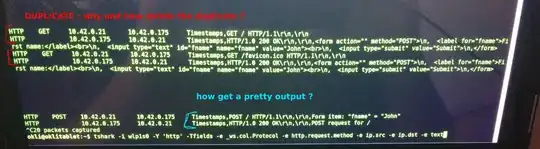
First, from the browser in the computer 10.42.0.21, when I enter the url of the server (a simple GET request) tshark shows the get request twice. I don't understand why.. is there a way for delete deplicate or find the reason ? (the server log show two GET requests)
secondly, when I send a POST request to the server (via a simple html form). We can see in plain text the datas of the form (it's logic because the server uses the HTTP protocole and not the HTTPS)
The curent output is : Timestamp,POST / HTTP/1.1\r\n,\r\n,Form item : "fname" = "John"
Is it possible with tshark to get a more prettiest output containing only the items (fields) values of the form ? like this : "fname" = "John"
Thanks for any help :)
EDIT : for the duplicate, this is because of a favicon request, the issue is from my python server, not from tshark.