I am working on implementing SPF and OpenDMARC/DKIM to my mail servers. Currently I have two mail servers in different subnets, each with separate DNS server and domain name. They can exchange emails successfully.
I set up SPF with pypolicyd-spf, DMARC with OpenDMARC and DKIM with OpenDKIM. DKIM works flawlessly, but I have some issues with DMARC and SPF, probably they are related to my topography (a graph of it is placed below).
I have users made on each mail server and I exchange mails between them via Squirrelmail.
How to make SPF and DMARC work? In my email headers I get:
Received-SPF: None (mailfrom) identity=mailfrom; client-ip=192.168.22.132
Authentication-Results: OpenDKIM; dmarc=none (p=none dis=none) header.from=another.com
I think there is something wrong with that localhost IP in logs but I have no idea what causes it:
policyd-spf[2183]: prepend X-Comment: SPF check N/A for local connections - client-ip=127.0.0.1; helo=[192.168.22.128]; envelope-from=centos1@example.com; receiver=<UNKNOWN>
postfix/smtpd[2177]: D5DA9C0F5F38: client=localhost[127.0.0.1]
my postconf -n output:
alias_database = hash:/etc/aliases
alias_maps = hash:/etc/aliases
command_directory = /usr/sbin
config_directory = /etc/postfix
daemon_directory = /usr/libexec/postfix
data_directory = /var/lib/postfix
debug_peer_level = 2
debugger_command = PATH=/bin:/usr/bin:/usr/local/bin:/usr/X11R6/bin ddd
$daemon_directory/$process_name $process_id & sleep 5
home_mailbox = Maildir/
html_directory = no
inet_interfaces = all
inet_protocols = ipv4
mail_owner = postfix
mailq_path = /usr/bin/mailq.postfix
manpage_directory = /usr/share/man
milter_default_action = accept
mydestination = $myhostname, localhost.$mydomain, localhost
mydomain = $myhostname
myhostname = example.com
mynetworks = 127.0.0.0/8, 192.168.22.0/24
myorigin = $myhostname
newaliases_path = /usr/bin/newaliases.postfix
non_smtpd_milters = $smtpd_milters
queue_directory = /var/spool/postfix
readme_directory = /usr/share/doc/postfix-2.10.1/README_FILES
sample_directory = /usr/share/doc/postfix-2.10.1/samples
sendmail_path = /usr/sbin/sendmail.postfix
setgid_group = postdrop
smtpd_milters = inet:127.0.0.1:8891, inet:127.0.0.1:8893
smtpd_recipient_restrictions = check_policy_service unix:private/policy-spf, permit_mynetworks,
reject_unauth_destination
unknown_local_recipient_reject_code = 550
Network graph:
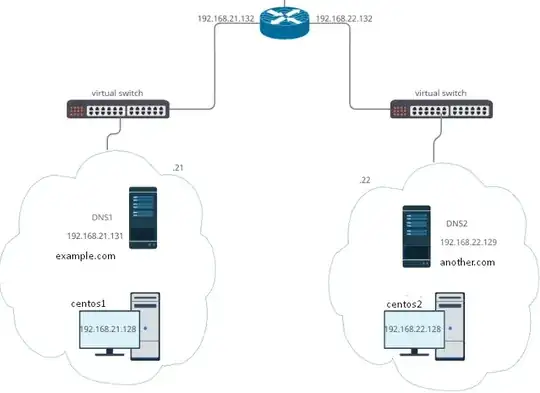
I can provide any additional info if needed.
Of course all entries in DNS are made.
example.com. IN TXT "v=spf1 mx ~all"
default._domainkey IN TXT ( "v=DKIM1; k=rsa; "
"p=XXXkeyXXX" ) ; ----- DKIM key default for example.com
_dmarc.example.com. IN TXT "v=DMARC1; p=none; pct=100"
policyd-spf logs:
policyd-spf[2681]: Read line: "request=smtpd_access_policy"
policyd-spf[2681]: Read line: "protocol_state=RCPT"
policyd-spf[2681]: Read line: "protocol_name=ESMTP"
policyd-spf[2681]: Read line: "client_address=192.168.22.132"
policyd-spf[2681]: Read line: "client_name=gateway"
policyd-spf[2681]: Read line: "reverse_client_name=gateway"
policyd-spf[2681]: Read line: "helo_name=example.com"
policyd-spf[2681]: Read line: "sender=daniel@example.com"
policyd-spf[2681]: Read line: "recipient=marek@another.com"
policyd-spf[2681]: Read line: "recipient_count=0"
policyd-spf[2681]: Read line: "queue_id="
policyd-spf[2681]: Read line: "instance=a73.5fe8c4e7.510b9.0"
policyd-spf[2681]: Read line: "size=935"
policyd-spf[2681]: Read line: "etrn_domain="
policyd-spf[2681]: Read line: "stress="
policyd-spf[2681]: Read line: "sasl_method="
policyd-spf[2681]: Read line: "sasl_username="
policyd-spf[2681]: Read line: "sasl_sender="
policyd-spf[2681]: Read line: "ccert_subject="
policyd-spf[2681]: Read line: "ccert_issuer="
policyd-spf[2681]: Read line: "ccert_fingerprint="
policyd-spf[2681]: Read line: "ccert_pubkey_fingerprint="
policyd-spf[2681]: Read line: "encryption_protocol="
policyd-spf[2681]: Read line: "encryption_cipher="
policyd-spf[2681]: Read line: "encryption_keysize=0"
policyd-spf[2681]: Read line: ""
policyd-spf[2681]: Found the end of entry
policyd-spf[2681]: Config: {'Whitelist_Lookup_Time': 10, 'skip_addresses': '127.0.0.0/8,::ffff:127.0.0.0/104,::1', 'Reason_Message': 'Message {rejectdefer} due to: {spf}. Please see {url}', 'PermError_reject': 'False', 'Header_Type': 'SPF', 'TestOnly': 0, 'SPF_Enhanced_Status_Codes': 'Yes', 'TempError_Defer': 'False', 'Lookup_Time': 20, 'debugLevel': 4, 'Authserv_Id': 'centos2.another.agh.edu.pl', 'Mail_From_reject': 'Fail', 'Hide_Receiver': 'Yes', 'HELO_reject': 'Fail', 'Void_Limit': 2, 'Mock': False}
Dec 27 12:31:19 centos2 policyd-spf[2681]: Cached data for this instance: []
Dec 27 12:31:19 centos2 policyd-spf[2681]: skip_addresses enabled.
Dec 27 12:31:29 centos2 policyd-spf[2681]: spfcheck: pyspf result: "['None', '', 'helo']"
Dec 27 12:31:29 centos2 policyd-spf[2681]: None; identity=no SPF record; client-ip=192.168.22.132; helo=example.com; envelope-from=daniel@example.com; receiver=<UNKNOWN>
Dec 27 12:31:29 centos2 policyd-spf[2681]: spfcheck: pyspf result: "['None', '', 'mailfrom']"
Dec 27 12:31:29 centos2 policyd-spf[2681]: None; identity=mailfrom; client-ip=192.168.22.132; helo=example.com; envelope-from=daniel@example.agh.edu.pl; receiver=<UNKNOWN>
Dec 27 12:31:29 centos2 policyd-spf[2681]: not peruser
Dec 27 12:31:29 centos2 policyd-spf[2681]: Action: prepend: Text: Received-SPF: None (mailfrom) identity=mailfrom; client-ip=192.168.22.132; helo=example.com; envelope-from=daniel@example.com; receiver=<UNKNOWN> Reject action: 550 5.7.23