RFC standards literally force us to accept unencrypted connections on port 25. To understand why, we have to understand how emailing works. But emailing is quite a complex topic and I created this example together with a table to try and understand everything.
Can anyone read and tell me if I am wrong in any part of the explanation? Because I am not quite sure if my understanding of the topic is correct.
EXAMPLE
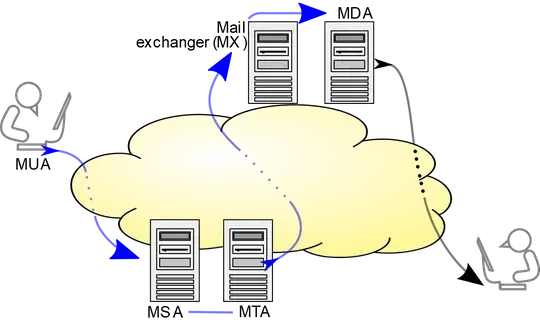
When user (sender) sends email through "mail user agent" (MUA), this email is immediately transfered to the "mail submission agent" (MSA) which is or isn't on a separate machine. MSA preprocesses the email and hand it over to "mail transfer agent" (MTA) on the same machine. MTA (sender) then uses DNS and determines to which MTA (receiver) email should be sent. This portion of the transport is only done over port 25. When the MTA (reciever) gets the email, it handles it over to the MSA on the same machine and then user (receiver) can read the email using MUA.
Communication between MUA & MSA and MSA & MTA can use secure ports but connection betweem MTA & MTA can't. Table below shows which protocols are used or can be used and which ports can be used for each step of the above example. We also use ✘ and ✔ where there is a choice to indicate what a modern setup should use.
| # | sender | receiver | protocols we can use | ports of respective protocols |
|---|---|---|---|---|
| 1 | MUA | MSA | (✘) SMTP (✔) SMTPS |
(✘) 25 (✔) 587 |
| 2 | MSA | MTA | (✘) SMTP (✔) SMTPS |
(✘) 25 (✔) 587 |
| 3 | MTA | MTA | (✔) SMTP | (✔) 25 |
| 4 | MTA | MSA | (✔) SMTP | (✔) 25 |
| 5 | MSA | MUA | (✘) POP3 (✘) POP3S (✘) IMAP (✔) IMAPS |
(✘) 110 (✘) 995 (✘) 143 (✔) 993 |