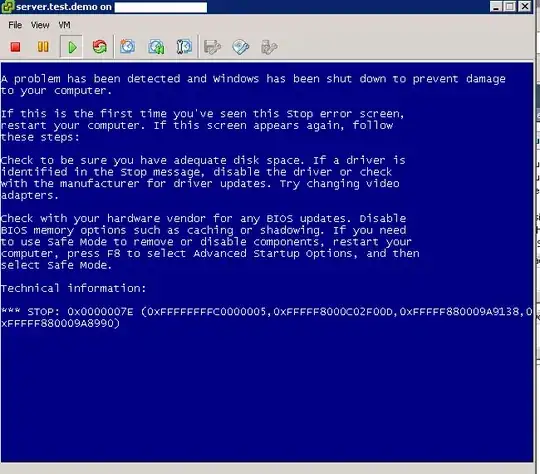
I have two network segments connected using a IPSEC-VPN tunnel :
- NET#1: a.b.0.0/16 with LAN gateway a.b.0.1
- NET#2: x.y.0.0/16 with LAN gateway x.y.130.1
I initiate a ping from a.b.0.1 to x.y.130.100 and started a tcpdump. This later shows echo replies packets but it doesn't show echo request packets.
Is it normal? How can I get the echo request packets too?
Here is a sample tests session:
The PING:
# ping x.y.130.100
PING x.y.130.100 56(84) bytes of data.
64 bytes from x.y.130.100: icmp_seq=1 ttl=63 time=1.87 ms
64 bytes from x.y.130.100: icmp_seq=2 ttl=63 time=1.38 ms
64 bytes from x.y.130.100: icmp_seq=3 ttl=63 time=1.27 ms
64 bytes from x.y.130.100: icmp_seq=4 ttl=63 time=3.93 ms
64 bytes from x.y.130.100: icmp_seq=5 ttl=63 time=1.15 ms
64 bytes from x.y.130.100: icmp_seq=6 ttl=63 time=1.16 ms
The TCPDUMP:
# tcpdump -nn 'icmp and (src a.b.0.1 or dst a.b.0.1)'
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
13:54:27.607103 IP x.y.130.100 > a.b.0.1: ICMP echo reply, id 22607, seq 1, length 64
13:54:28.608433 IP x.y.130.100 > a.b.0.1: ICMP echo reply, id 22607, seq 2, length 64
13:54:29.610167 IP x.y.130.100 > a.b.0.1: ICMP echo reply, id 22607, seq 3, length 64
13:54:30.614716 IP x.y.130.100 > a.b.0.1: ICMP echo reply, id 22607, seq 4, length 64
13:54:31.613417 IP x.y.130.100 > a.b.0.1: ICMP echo reply, id 22607, seq 5, length 64
13:54:32.615054 IP x.y.130.100 > a.b.0.1: ICMP echo reply, id 22607, seq 6, length 64