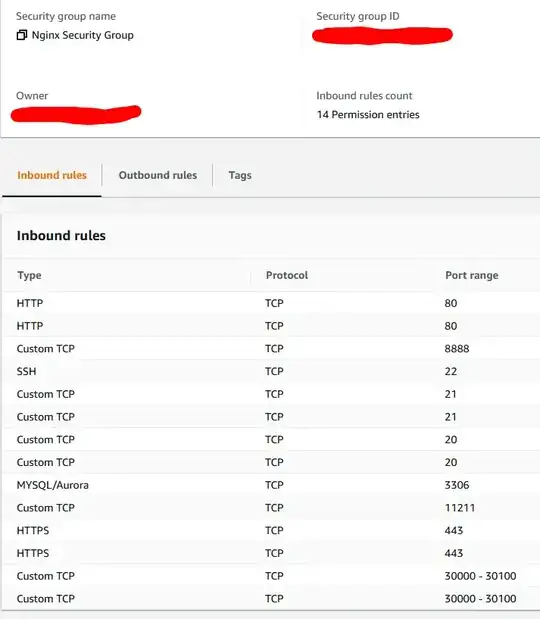
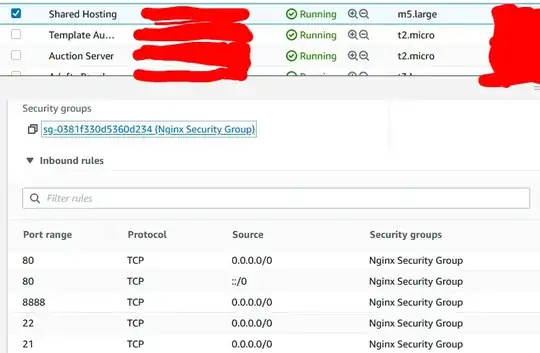
I have recently installed OSSEC on a RHEL 8 server being hosted on AWS EC2. Since then I have been receiving brute force attempts and other attempts on ports that are not open in my security group.
How are users able to get to my server at all when these ports are not open in the security group for the EC2 instance, and how do I stop them from reaching the server at all?
Example report:
OSSEC HIDS Notification. 2020 Oct 18 20:45:33
Received From: shared->/var/log/secure Rule: 5712 fired (level 10) -> "SSHD brute force trying to get access to the system." Src IP: 46.101.209.127 Portion of the log(s):
Oct 18 20:45:32 shared sshd[3097608]: Disconnected from invalid user pi 46.101.209.127 port 49568 [preauth] Oct 18 20:45:32 shared sshd[3097608]: Invalid user pi from 46.101.209.127 port 49568 Oct 18 20:45:12 shared sshd[3097603]: Disconnected from invalid user admin 46.101.209.127 port 58720 [preauth] Oct 18 20:45:12 shared sshd[3097603]: Invalid user admin from 46.101.209.127 port 58720 Oct 18 20:44:51 shared sshd[3097591]: Disconnected from invalid user admin 46.101.209.127 port 39802 [preauth] Oct 18 20:44:50 shared sshd[3097591]: Invalid user admin from 46.101.209.127 port 39802 Oct 18 20:44:30 shared sshd[3097582]: Disconnected from invalid user admin 46.101.209.127 port 49134 [preauth] Oct 18 20:44:30 shared sshd[3097582]: Invalid user admin from 46.101.209.127 port 49134
--END OF NOTIFICATION