I'm running Windows Server 2016 Active Passive ADFS server, the below issue is happening on the passive node.
AD domain is single AD domain: domain.com The same Wildcard SSL certificate has been imported successfully to the other ADFS 2016 servers with no issue.
When I upload the ADFS Server 2016 logs into https://adfshelp.microsoft.com/DiagnosticsAnalyzer/Analyze
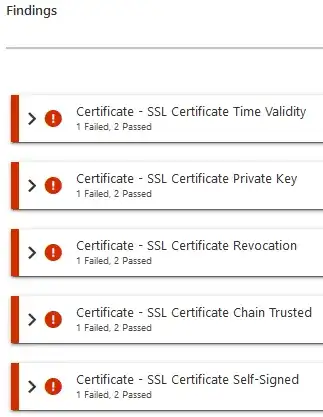
I got the below error like in the screenshot.
The description of the error is:
The diagnostic threw an unhandled exception.
System.ArgumentOutOfRangeException: Index was out of range. Must be non-negative and less than the size of the collection.
at System.ThrowHelper.ThrowArgumentOutOfRangeException(ExceptionArgument argument, ExceptionResource resource)
at System.Collections.Generic.List`1.get_Item(Int32 index)
at Microsoft.Identity.Federation.AdfsToolbox.Core.Framework.PowerShell.PowerShellProvider.GetAdfsSslCertificate()
at Microsoft.Identity.Federation.AdfsToolbox.Core.Framework.PowerShell.PowerShellProvider.GetFederationCertificate(FederationCertificateType type)
at Microsoft.Identity.Federation.AdfsToolbox.Core.Diagnostics.Modules.CertificateValidity.SslValidity.GetCertificate()
at Microsoft.Identity.Federation.AdfsToolbox.Core.Diagnostics.Modules.CertificateValidity.ValidityBase.RunDiagnostic()
at Microsoft.Identity.Federation.AdfsToolbox.Core.Diagnostics.Modules.DiagnosticModuleBase.Execute()
The result from Active ADFS server node: Get-AdfsSslCertificate
HostName PortNumber CertificateHash
-------- ---------- ---------------
ADFS.domain.com 443 CFHH542125AE8C06F4968AF2468E62699124AF52
localhost 443 CFHH542125AE8C06F4968AF2468E62699124AF52
ADFS.domain.com 49443 CFHH542125AE8C06F4968AF2468E62699124AF52
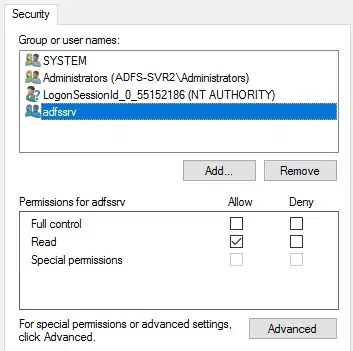
This is the Private key permission from the passive /secondary server that failed:
After remote desktop into PRDADFS2-VM (secondary server)
I have already manually imported the *.domain.com SSL certificate.PFX file.
Add-AdfsFarmNode -ServiceAccountCredential (Get-Credential) -PrimaryComputerName PRDADFS1-VM.domain.com -CertificateThumbprint CFHH542125AE8C06F4968AF2468E62699124AF53 -OverwriteConfiguration
The result is:
WARNING: The SSL certificate subject alternative names do not support hostname 'certauth.ADFS.domain.com'. Configuring certificate authentication binding on port '49443' and hostname ' ADFS.domain.com'.
WARNING: Failed to register SSL bindings for Device Registration Service: An item with the same key has already been added.