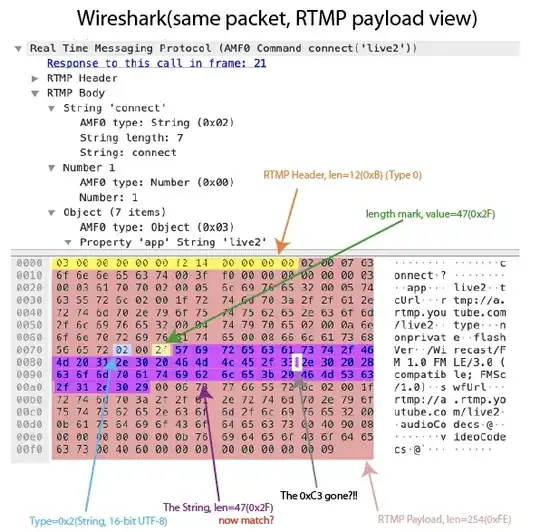
I'm analyzing the RTMP(Real-Time Messaging Protocol) and found something really weird. In one of the captured packets, the TCP payload length is longer than expected. Here's the packet in Wireshark:
The C3 byte makes the RTMP longer than expected. Which surprisingly gone in the RTMP payload view:
As you can see, the C3 byte disappeared in the RTMP view. But it is part of the TCP payload. I can't get an idea why this happen, I suspect:
Some longer UTF-8 character?
According to wikipedia, the string in AMF0 is encoded into 16-bit UTF-8. It means it can be either 8/16bit. However,
\u33C3and\uC32Eare both Korean characters, which shown in the second picture that it isn't my case.Padding / escape character for TCP payload?
Nah...I never heard about that...
Something about TCP that I don't know?
Here's what I found:
a. It wasn't a fragment of RTMP message, the TCP packet hold everything a RTMP message need.
b. The checksum is good, everything seems good.
c. The packet was correctly ACK-ed by peer (not shown in picture)
d. This is reproduce-able, by using the streaming software Wirecast
Am I missing something here? Why could Wireshark correctly decode the payload? Why Wireshark simply remove the C3 (that suggests it has nothing to do with AMF0 codec)? I'm so confuse. Please help :'(
RTMP protocol specifications here: https://wwwimages2.adobe.com/content/dam/acom/en/devnet/rtmp/pdf/rtmp_specification_1.0.pdf