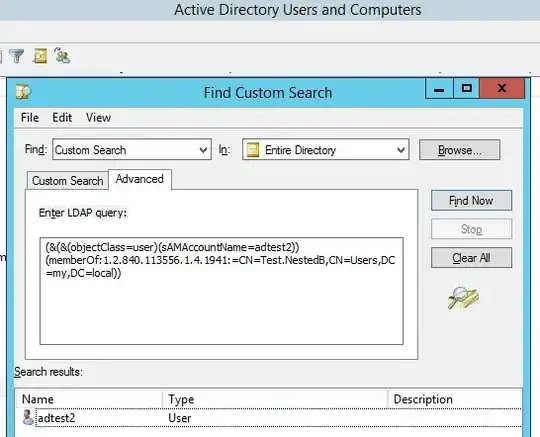
I have a single domain (my.local) with 2 domain controllers:
- 192.168.3.63 - DC1
- 192.168.3.64 - DC2 (primary DC)
I'm testing request to find if user is a member of a group. Here's a query filter:
(&(&(objectClass=user)(sAMAccountName=adtest2))(memberOf:1.2.840.113556.1.4.1941:=CN=Test.NestedB,CN=Users,DC=my,DC=local))
And If I use "Active Directory Users and Computers" (ADUaC) snap-in on both controllers I get the same result:
But when I run dsquery, I get no results:
C:\Users\admin>dsquery * domainroot -filter "(&(&(objectClass=user)(sAMAccountName=adtest2))(memberOf:1.2.840.113556.1.4.1941:=CN=Test.NestedB,CN=Users,DC=my,DC=local))"
C:\Users\admin>
What is more interesting is that if I specify the -s paramter, dsquery returns the results, BUT only when I pass another DC, not the one from which I run dsquery
On DC1 (192.168.3.63): notice the change in behavior depending on the -s switch
C:\Users\admin>dsquery * domainroot -s 192.168.3.63 -filter "(&(&(objectClass=user)(sAMAccountName=adtest2))(memberOf:1.2.840.113556.1.4.1941:=CN=Test.NestedB,CN=Users,DC=my,DC=local))"
C:\Users\admin>
C:\Users\admin>dsquery * domainroot -s 192.168.3.64 -filter "(&(&(objectClass=user)(sAMAccountName=adtest2))(memberOf:1.2.840.113556.1.4.1941:=CN=Test.NestedB,CN=Users,DC=my,DC=local))"
"CN=adtest2,CN=Users,DC=my,DC=local"
C:\Users\admin>
On DC2 (192.168.3.64):
C:\Users\admin>dsquery * domainroot -s 192.168.3.63 -filter "(&(&(objectClass=user)(sAMAccountName=adtest2))(memberOf:1.2.840.113556.1.4.1941:=CN=Test.NestedB,CN=Users,DC=my,DC=local))"
"CN=adtest2,CN=Users,DC=my,DC=local"
C:\Users\admin>
C:\Users\admin>dsquery * domainroot -s 192.168.3.64 -filter "(&(&(objectClass=user)(sAMAccountName=adtest2))(memberOf:1.2.840.113556.1.4.1941:=CN=Test.NestedB,CN=Users,DC=my,DC=local))"
C:\Users\admin>
I tried dsquery to run with domainroot, forestroot and "DC=my,DC=local" - with no effect.
I also tried to specify -scope subtree, but this is the default BTW.
- Why dsquery without specifying DC always fails to find user and ADUaC alays succeeds?
- Why dsquery returns result only from a different DC, but on from current DC when -s switch is specified?
- What can/should I chage in order to make dsquery work consistently?